Hoje, você pode entregar aplicações modernas mais rápido do que nunca. A IA escreve metade do seu código, pipelines são implantados em minutos, e sua equipe está produzindo funcionalidades como se cada dia fosse o fim do mundo.
Mas aqui está uma pergunta para você: o que está acompanhando a segurança?
Porque a velocidade no desenvolvimento de software tem um lado sombrio. Você pode chamar de negligência, erro humano ou o velho ditado “Eu vou resolver isso depois”, bem, é assim que bugs, configurações incorretas e vulnerabilidades completas se infiltram na produção sem que ninguém perceba. E os atacantes? Eles só precisam de uma.
É por isso que Testes Dinâmicos de Segurança de Aplicações (DAST) importam em 2025. Para garantir que o que você implantou esteja seguro e protegido.
Neste guia, detalhamos:
- O que é DAST
- Por que isso importa em 2025, e
- Como escolher a ferramenta DAST certa para sua equipe, seja você um desenvolvedor solo ou um líder de segurança empresarial.
Para facilitar, você não precisa se aprofundar em todas as mais de 15 ferramentas. Se você está aqui com um caso de uso específico em mente — digamos que você esteja procurando o melhor DAST para desenvolvedores, startups ou segurança de API — sinta-se à vontade para ir direto para as sublistas adaptadas ao seu cenário.
- As 5 Melhores Ferramentas DAST para Desenvolvedores: Aikido Security & Burp Suite
- As 6 Melhores Ferramentas DAST para Empresas: Invicti & Aikido Security
- As 4 Melhores Ferramentas DAST para Startups: Aikido Security & OWASP ZAP
- As 4 Melhores Ferramentas DAST Gratuitas: Wapiti & Arichni
- As 4 Melhores Ferramentas DAST de Código Aberto: OWASP ZAP & Nikto
- As 6 Melhores Ferramentas DAST para DevSecOps: Aikido Security & Invicti
- As 6 Melhores Ferramentas DAST para Segurança de API: Qualys & Aikido Security
- As 6 Melhores Ferramentas DAST para Aplicações Web: Aikido Security & Burp Suite
- As 6 Melhores Ferramentas DAST para REST APIs: Tenable & Wapiti
- As 6 Melhores Ferramentas DAST para Aplicativos Móveis: OWASP ZAP & HCL Appscan
Dito isso, recomendamos verificar a análise completa das ferramentas mais abaixo. Mesmo uma leitura rápida da lista principal pode revelar uma ferramenta que você não havia considerado, ou ajudar a entender por que algumas opções consistentemente se destacam em várias categorias.
TL;DR:
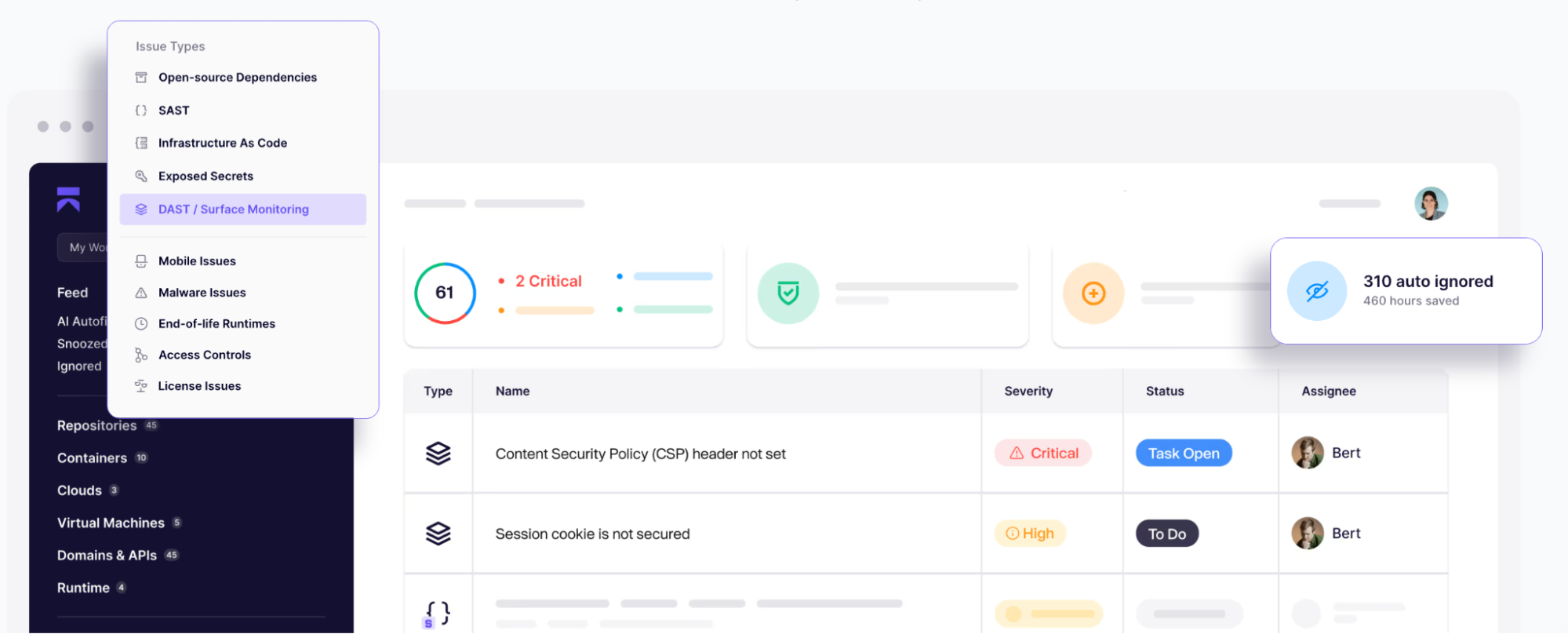
Aikido se destaca como a principal escolha de DAST ao agrupar um poderoso scanner DAST com SAST, segurança de API e muito mais em uma única plataforma. Seu DAST de “Surface Monitoring” ataca seu aplicativo como um hacker, mas com muito menos falsos positivos graças à verificação e filtragem integradas.
Desenvolvedores obtêm correções com um clique para descobertas e integração CI/CD pronta para uso, e gerentes técnicos apreciam o preço transparente de taxa fixa da Aikido (além de um plano gratuito) em comparação com as surpresas das ferramentas DAST legadas.
O que é DAST?
Testes Dinâmicos de Segurança de Aplicações (DAST) é um método de teste de segurança que avalia uma aplicação em execução de fora para dentro, de forma semelhante a como um atacante faria. Uma ferramenta DAST interage com uma aplicação web através do seu frontend (requisições HTTP, interfaces web, APIs) sem a necessidade de acesso ao código-fonte.
A abordagem “black-box” do DAST envolve simular entradas maliciosas e analisar as respostas da aplicação para identificar vulnerabilidades como SQL injection, cross-site scripting (XSS), falhas de autenticação, configurações incorretas e outros problemas de tempo de execução. Em essência, o DAST se comporta como um hacker automatizado sondando as defesas da sua aplicação.
As soluções DAST são distintas das ferramentas de análise estática (SAST) porque elas testam a aplicação em execução em um ambiente realista. Enquanto o SAST escaneia o código-fonte em busca de bugs, o DAST de fato lança ataques em uma aplicação implantada para verificar se essas vulnerabilidades podem ser exploradas em tempo real.
O DAST é frequentemente utilizado em testes de estágio avançado (QA, staging, ou até mesmo em produção com cautela) como uma verificação final para identificar qualquer coisa que tenha sido perdida anteriormente.
Em 2025, o DAST continua crucial porque as aplicações web modernas são cada vez mais complexas (single-page apps, microsserviços, APIs, etc.). As ferramentas DAST evoluíram para lidar com esses desafios, incluindo:
- rastreamento de interfaces ricas,
- seguindo redirecionamentos,
- lidando com fluxos de autenticação, e
- testando APIs REST/GraphQL,
Tudo isso sem a necessidade de ver os internos da aplicação.
Muitas organizações adotam uma estratégia combinada de SAST e DAST para uma cobertura abrangente em todo o ciclo de vida de desenvolvimento de software. Para uma comparação mais aprofundada, consulte nosso guia sobre como usar SAST e DAST juntos.
Por que você precisa de ferramentas DAST
Antes de mergulharmos nas ferramentas em si, como mencionado anteriormente, qual é o sentido de adicionar mais um scanner à sua stack?
Bem, a base é que a segurança de aplicações web é um alvo em constante movimento. Com as aplicações mudando tão rapidamente e os atacantes descobrindo constantemente novas formas de explorá-las.
O uso de ferramentas DAST é essencial em 2025 porque você obtém:
- Cobertura no Mundo Real: As ferramentas DAST encontram vulnerabilidades a partir da perspectiva de um atacante, mostrando exatamente o que um invasor poderia explorar em uma aplicação em execução. Elas podem descobrir problemas no ambiente (configurações de servidor, componentes de terceiros, APIs) que as verificações de código estático podem não detectar.
- Independente de Linguagem e Plataforma: Como o DAST interage com a aplicação via HTTP e a UI, não importa em qual linguagem ou framework a aplicação foi escrita. Um scanner DAST pode testar Java, Python, Node ou qualquer plataforma web, o que é ideal para ambientes poliglota.
- Encontra Bugs Críticos em Tempo de Execução: O DAST se destaca em detectar problemas como servidores mal configurados, fluxos de autenticação quebrados, cookies inseguros e outros problemas de implantação que só aparecem quando a aplicação está ativa. Estas são frequentemente vulnerabilidades de alto impacto que passam despercebidas nas revisões de código.
- Baixos Falsos Positivos (em muitos casos): Soluções DAST modernas usam técnicas como verificação de ataque (por exemplo, prova de exploração) para confirmar vulnerabilidades e reduzir ruído. Ao contrário do SAST, que pode sinalizar problemas teóricos, o DAST geralmente mostra evidências concretas (como “O cookie de sessão não está seguro”), tornando mais fácil para os desenvolvedores confiarem nos resultados.
- Conformidade e Tranquilidade: Muitos padrões e regulamentações de segurança (PCI DSS, Top 10 OWASP, etc.) recomendam ou exigem testes dinâmicos de aplicações web. Usar uma ferramenta DAST ajuda a cumprir esses requisitos, produzindo relatórios que os auditores entendem (por exemplo, cobertura de problemas do Top 10 OWASP) e garante que você não deixou grandes lacunas em sua aplicação antes do lançamento.
Em resumo, o DAST adiciona uma camada essencial de segurança ao atacar sua aplicação da mesma forma que ameaças reais fariam, para que você possa corrigir as fraquezas antes que agentes mal-intencionados as explorem.
Como Escolher uma Ferramenta DAST
Nem todos os scanners DAST são iguais. Ao avaliar ferramentas de Testes Dinâmicos de Segurança de Aplicações, considere os seguintes critérios para encontrar a melhor opção:
- Cobertura de Tecnologias: Garanta que a ferramenta possa lidar com a stack de tecnologia de suas aplicações. Ela suporta frontends modernos com uso intensivo de JavaScript (Single Page Applications), backends móveis e APIs (REST, SOAP, GraphQL)? Ferramentas como HCL AppScan e Invicti suportam uma ampla gama de tipos de aplicações.
- Precisão e Profundidade: Procure por altas taxas de detecção de vulnerabilidades com mínimos falsos positivos. Recursos como scans de confirmação ou geração de prova de conceito (por exemplo, o scanning baseado em prova do Aikido e Invicti) são valiosos para validar automaticamente as descobertas. Você quer uma ferramenta que descubra problemas críticos, mas que não o sobrecarregue com ruído.
- Facilidade de Uso e Integração: Um bom DAST se encaixa no seu fluxo de trabalho. Considere ferramentas que ofereçam configuração fácil (opções baseadas em Cloud ou gerenciadas), integração CI/CD para DevSecOps (Aikido, StackHawk, etc.) e integrações com rastreadores de problemas (Jira, GitHub) ou fluxos de trabalho. Se seus desenvolvedores puderem acionar scans a partir de pipelines e obter resultados em suas ferramentas, a adoção será mais suave.
- Autenticação e Tratamento de Complexidade: Muitos aplicativos não são totalmente públicos, por isso é importante verificar se o seu DAST suporta varredura autenticada (login com uma conta de usuário/sessão) e pode lidar com coisas como formulários de várias etapas ou fluxos complexos. Scanners de nível empresarial como Burp Suite, AppScan e outros permitem o registro de sequências de login ou scripts de autenticação.
- Relatórios e Feedback do Desenvolvedor: A saída deve ser amigável para desenvolvedores. Procure por descrições claras de vulnerabilidades, orientações de remediação e relatórios de conformidade, se necessário (por exemplo, relatórios mapeados para Top 10 OWASP, PCI, etc.). Algumas plataformas (como o DAST da Aikido) até fornecem sugestões de correção automáticas ou patches de código para acelerar a remediação.

- Escalabilidade e Desempenho: Se você precisa escanear dezenas ou centenas de aplicativos, considere como a ferramenta escala. Serviços DAST baseados em Cloud (Qualys WAS, Rapid7 InsightAppSec, Tenable.io, etc.) podem executar varreduras em paralelo e gerenciar o agendamento. Também avalie a velocidade da varredura, pois algumas ferramentas oferecem varredura incremental ou otimização para retestes mais rápidos.
- Suporte e Manutenção: Finalmente, uma ferramenta é tão boa quanto sua última atualização. Avalie a frequência com que o fornecedor atualiza as verificações de vulnerabilidade do scanner.
Uma comunidade ativa ou suporte do fornecedor é crucial, especialmente para opções de código aberto. Um DAST desatualizado (ou um sem suporte) pode perder novas ameaças ou falhar em aplicativos modernos.
Mantenha esses critérios em mente ao revisar o cenário das soluções DAST. Agora, vamos mergulhar nas principais ferramentas disponíveis em 2025 e ver como elas se comparam.
As 12 Melhores Ferramentas DAST para 2025
Nesta seção, listamos as 12 melhores ferramentas de Testes Dinâmicos de Segurança de Aplicações de 2025. Estas incluem uma mistura de opções comerciais e de código aberto, cada uma com pontos fortes únicos.
Para cada ferramenta, compartilhamos suas principais características, casos de uso ideais, informações de preços e até mesmo alguns trechos de avaliações de usuários.
Seja você um desenvolvedor em uma startup ou um líder de segurança em uma empresa, você encontrará uma solução DAST que se adapta às suas necessidades.
Antes de mergulharmos na lista, aqui está uma comparação das 5 principais ferramentas DAST gerais com base em recursos como varredura de API, integração CI/CD e precisão.
Essas ferramentas são as melhores da categoria para uma variedade de necessidades, desde desenvolvedores até equipes empresariais.
1. Acunetix by Invicti
Acunetix by Invicti é um scanner de vulnerabilidades web focado em DAST, projetado para organizações de pequeno e médio porte. Ele oferece varredura automatizada de sites e APIs, com ênfase na implantação rápida. O Acunetix surgiu como um produto autônomo e agora faz parte da família de produtos da Invicti Security (complementando o scanner Invicti de nível empresarial). Ele oferece um ponto de entrada para equipes que estão iniciando seu programa de segurança de aplicações.
Principais recursos:
- Cobertura de Vulnerabilidades: Varre mais de 7.000 vulnerabilidades web conhecidas, incluindo todos os problemas do Top 10 OWASP, com verificações para SQLi, XSS, configurações incorretas, senhas fracas e muito mais.
- Varredura Baseada em Provas: Utiliza a tecnologia proprietária de prova de exploração da Invicti para verificar automaticamente muitas descobertas, reduzindo falsos positivos. Por exemplo, pode confirmar com segurança injeções SQL demonstrando uma amostra de extração de dados.
- Varredura de API e SPA: O Acunetix pode lidar com aplicações modernas. Ele pode rastrear aplicações de página única HTML5 e testar APIs REST e GraphQL. Também suporta a importação de definições Swagger/OpenAPI para garantir cobertura completa da API.
- Integrações e CI/CD: Oferece integrações nativas com rastreadores de issues (como Jira) e pipelines de CI/CD (Jenkins, GitLab CI, etc.) para habilitar a automação em DevSecOps. As varreduras podem ser acionadas em novas builds, e os resultados exportados como tickets de desenvolvedor para ciclos de correção rápidos.
- Conformidade e Relatórios: Fornece relatórios de conformidade prontos para padrões como Top 10 OWASP, PCI DSS, HIPAA, ISO 27001, e mais – útil para auditorias e para demonstrar testes de segurança aos stakeholders.
Destaque da avaliação: “Acunetix possui uma UI amigável, é fácil de configurar e executar, e produz resultados confiáveis. O modelo de licenciamento não é tão granular quanto poderia ser, o que significa que é necessário planejamento para escalar para cima ou para baixo.” (Fonte: G2)
2. Aikido Security

O DAST da Aikido Security (chamado Surface Monitoring) simula ataques black-box em seu aplicativo web para encontrar vulnerabilidades em tempo real.
O que diferencia a Aikido é que, além do monitoramento de superfície de aplicativos front-end e hospedados, ela oferece DAST autenticado para testar dinamicamente seu aplicativo web por trás da autenticação. Além disso, sua abordagem modular é única, pois reúne DAST, SAST, varredura de segurança de API, verificações de configuração de Cloud e muito mais em uma única interface, proporcionando uma experiência fluida para desenvolvedores e equipes de segurança. A plataforma é baseada em Cloud, com um nível gratuito generoso, tornando a segurança de nível empresarial acessível a startups e grandes empresas.
Principais recursos:
- SAST + DAST Unificados: A Aikido combina testes estáticos e dinâmicos – você pode identificar problemas precocemente com SAST e verificá-los em aplicativos em execução com DAST. Todos os resultados são direcionados para um único dashboard para uma visibilidade holística de AppSec (caso de uso SAST e DAST juntos).
- Monitoramento de front-end e hospedado: Teste dinamicamente as superfícies de front-end e de aplicativos hospedados do seu aplicativo web para encontrar vulnerabilidades via ZAP ou Nuclei.
- DAST Autenticado: A Aikido se diferencia de outros provedores de SAST+DAST por ser capaz de testar dinamicamente seu aplicativo web por trás da autenticação para descobrir vulnerabilidades com ataques simulados. É um pentest automatizado de caixa cinza.
- Fluxo de Trabalho Amigável ao Desenvolvedor: Projetado para ser “segurança sem complicação para desenvolvedores.” A Aikido se integra com ferramentas de desenvolvimento (IDEs, pipelines de CI/CD, GitHub/GitLab, alertas do Slack). Os desenvolvedores recebem feedback imediato – por exemplo, as descobertas de DAST podem aparecer como comentários de pull request ou resultados de pipeline, com links para sugestões de correção. Um usuário disse: “Com a Aikido, a segurança é apenas parte da forma como trabalhamos agora. É rápido, integrado e realmente útil para os desenvolvedores.”
- Descoberta e Varredura Automatizada de API: O motor DAST inclui descoberta automatizada de endpoints de API (REST e GraphQL) e os verifica em busca de vulnerabilidades. Isso é crucial, pois as APIs frequentemente acompanham aplicativos web modernos. A Aikido também pode fazer login e testar áreas autenticadas, aumentando a cobertura da superfície de ataque do seu aplicativo.
- Autofix Alimentado por IA: Um recurso de destaque. A plataforma da Aikido pode gerar correções com um clique para certas descobertas usando IA. Por exemplo, se o DAST encontrar um XSS refletido, a plataforma pode sugerir um patch de código ou uma alteração de configuração. Isso transforma as descobertas de segurança em tarefas acionáveis que os desenvolvedores podem resolver em segundos.

- Escalabilidade e Integração com a Cloud: Sendo um serviço Cloud, o Aikido escala para escanear continuamente muitas aplicações. É adequado para escala corporativa (acesso baseado em função, dashboards de equipe para uso Enterprise, etc.), mas também muito acessível para equipes enxutas. A plataforma pode ser executada na sua CI, ou você pode acionar scans sob demanda por meio de uma interface web simples ou API.
Destaque da avaliação: “Com o Aikido, podemos corrigir um problema em apenas 30 segundos – clique em um botão, faça o merge do PR, e está feito.” (Feedback do usuário sobre auto-remediação)
Proteja Seus Apps e APIs
Surface & Auth DAST
3. Burp Suite
Burp Suite da PortSwigger é uma ferramenta lendária no mundo da segurança web. É uma plataforma integrada que suporta testes de segurança de aplicações web manuais e automatizados.
O Burp Suite é amplamente utilizado por penetration testers, bug bounty hunters e profissionais de segurança. Ele opera como um proxy interceptador (permitindo modificar o tráfego) e inclui um scanner automatizado (Burp Scanner) para DAST. As ferramentas modulares da suíte (Proxy, Scanner, Intruder, Repeater, etc.) fornecem um kit de ferramentas de hacking abrangente.
Principais recursos:
- Proxy Interceptador: No núcleo do Burp está um proxy que intercepta requisições e respostas HTTP/S. Isso permite que os testers inspecionem e modifiquem o tráfego em tempo real. É inestimável para testes manuais, pois você pode manipular parâmetros, headers, etc., e então enviar requisições para outras ferramentas do Burp para testes adicionais.
- Scanner Automatizado: O scanner DAST do Burp pode rastrear automaticamente uma aplicação e buscar por vulnerabilidades. Ele reconhece mais de 300 tipos de vulnerabilidades de forma nativa, incluindo SQLi, XSS, CSRF, command injection e outros. Com mais de 2500 casos de teste e padrões, ele é bastante completo. Os resultados do scanner incluem evidências e orientações para remediação.
- Extensibilidade (BApp Store): O Burp possui um ecossistema de plugins extenso. A BApp Store oferece extensões desenvolvidas pela comunidade que adicionam funcionalidades, desde verificações de vulnerabilidade até integração com outras ferramentas. Isso significa que você pode estender o Burp para escanear ameaças emergentes ou integrar com pipelines de desenvolvimento (há até um plugin CI do Burp, e o Burp Enterprise é um produto separado para automação).
- Ferramentas de Teste Manual: Além da varredura, o Burp Suite se destaca com ferramentas como o Intruder (para fuzzing/força bruta automatizados), Repeater (para criar e reenviar requisições individuais), Sequencer (para análise de tokens) e Decoder/Comparer. Estas permitem que testadores experientes aprofundem-se em questões específicas sinalizadas pela varredura automatizada.
- Integração CI/CD: Para DevSecOps, a PortSwigger oferece o Burp Suite Enterprise (uma edição separada) que é projetado para executar varreduras em CI e em escala. Mas mesmo o Burp Pro pode ser usado em scripts via linha de comando ou API. Isso permite que as equipes incluam varreduras do Burp como parte de seu pipeline (frequentemente para aplicações críticas ou para verificar outros scanners).
Destaque da avaliação: “Uma das melhores ferramentas de proxy para bug bounty hunters e testadores de penetração. Não há o que não gostar; todo profissional adora.” (Avaliação G2)
4. HCL AppScan Standard

HCL AppScan Standard (anteriormente IBM AppScan) é uma ferramenta DAST baseada em desktop para usuários corporativos. Ela oferece um rico conjunto de recursos para varredura de aplicações web, serviços web e até mesmo alguns backends de aplicativos móveis em busca de vulnerabilidades de segurança.
O AppScan Standard faz parte do portfólio mais amplo do HCL AppScan (que também inclui AppScan Enterprise, AppScan on Cloud, ferramentas SAST, etc.). É conhecido por suas capacidades de varredura e é frequentemente utilizado por auditores de segurança e equipes de QA em grandes organizações.
Principais recursos:
- Mecanismo de Varredura: O AppScan Standard emprega algoritmos avançados de rastreamento e teste para maximizar a cobertura de aplicativos complexos. Sua varredura “Action-Based” pode lidar com aplicações de página única e código client-side rico. Ele também possui dezenas de milhares de casos de teste integrados cobrindo desde SQLi, XSS até falhas lógicas. É projetado para lidar com aplicativos web complexos com sequências de login, fluxos de trabalho multi-etapas e muito mais.
- Teste de API e Backend Móvel: Além dos aplicativos web tradicionais, ele pode testar APIs web (SOAP, REST) e backends móveis. Você pode fornecer definições de API ou registrar o tráfego móvel para auditar os endpoints. Isso torna o AppScan útil para empresas com aplicativos móveis que se comunicam com serviços JSON/REST.
- Varreduras Incrementais e Otimizadas: Para maior eficiência, o AppScan permite a varredura incremental, o que significa retestar apenas as partes novas ou alteradas de um aplicativo. Isso economiza tempo nos testes de regressão. Você também pode ajustar as configurações de velocidade de varredura vs. cobertura para se adequar a varreduras rápidas de desenvolvimento ou auditorias aprofundadas.
- Relatórios e Conformidade: O AppScan Standard possui recursos robustos de relatórios. Ele pode gerar uma variedade de relatórios, incluindo aqueles focados no desenvolvedor com recomendações de “correção” e resumos executivos. Notavelmente, ele oferece relatórios de conformidade e padrões da indústria (PCI, HIPAA, Top 10 OWASP, DISA STIGs, etc.), facilitando a demonstração de adesão aos requisitos de segurança.
- Integração Empresarial: Embora o AppScan Standard seja um cliente autônomo, ele pode se integrar ao AppScan Enterprise (para escalar varreduras em uma equipe) e a pipelines de CI/CD via execução por linha de comando ou APIs. A HCL também fornece plugins para ferramentas como Jenkins. Além disso, ele suporta varredura autenticada com vários mecanismos (Basic, NTLM, autenticação por formulário, etc.) e pode funcionar facilmente atrás do firewall corporativo, já que você o executa localmente.
Contexto da avaliação: A longevidade do AppScan no mercado (desde os tempos da IBM) significa que ele é testado e comprovado. Os usuários frequentemente elogiam sua profundidade, mas observam que a UI e a configuração podem ser complexas.
Se você investir tempo, ele encontrará vulnerabilidades de forma confiável e produzirá os relatórios necessários para satisfazer os auditores.
5. Micro Focus Fortify WebInspect

Micro Focus Fortify WebInspect (agora sob a OpenText, que adquiriu a Micro Focus) é uma ferramenta DAST de nível empresarial conhecida por seu uso em avaliações de segurança aprofundadas e integração com a suíte Fortify. O WebInspect oferece varredura dinâmica automatizada para aplicações e serviços web, e é frequentemente usado em conjunto com as ferramentas de análise estática (SAST) da Fortify para cobrir ambos os ângulos. Esta ferramenta tem uma longa história em AppSec e é preferida por organizações que exigem varredura on-premises e integração com programas mais amplos de gerenciamento de vulnerabilidades.
Principais recursos:
- Varredura Automatizada Abrangente: O WebInspect realiza varreduras rigorosas que podem identificar uma ampla gama de vulnerabilidades em aplicações web e APIs. Inclui verificações para o Top 10 OWASP, falhas de lógica de negócios e problemas de configuração de servidor. O scanner utiliza uma combinação de abordagens de assinatura e heurísticas para descobrir CVEs conhecidos, bem como problemas de dia zero (como casos extremos de tratamento de entrada incomuns).
- Análise de JavaScript e Client-side: Em versões recentes, o Fortify WebInspect melhorou na análise e parsing de código client-side. Ele pode executar JavaScript, lidar com aplicações com uso intenso de AJAX e até mesmo capturar comunicação de web Socket durante as varreduras (conforme suas atualizações de 2024). Isso significa que SPAs e frameworks web modernos podem ser auditados de forma mais eficaz.
- Integração com Fluxos de Trabalho Empresariais: O WebInspect se integra ao ecossistema Fortify. Por exemplo, os resultados podem fluir para o Fortify Software Security Center (SSC) para gerenciamento centralizado, correlação com resultados SAST e atribuição a desenvolvedores. Ele também possui APIs e suporte para automação, podendo ser integrado a pipelines de CI ou sistemas de orquestração de segurança. Muitas grandes organizações o utilizam em fluxos de trabalho de varredura agendada para monitoramento contínuo.
- Varreduras Autenticadas e com Estado: A ferramenta suporta uma variedade de métodos de autenticação (incluindo técnicas de múltiplos fatores, macros de login e autenticação baseada em OAuth/token). Ela pode manter o estado durante a varredura, o que é crucial para aplicações que exigem login e possuem fluxos de usuário complexos. O WebInspect também permite a gravação de macros para percorrer sequências específicas (como adicionar itens a um carrinho e depois finalizar a compra), garantindo que essas áreas sejam testadas.
- Relatórios e Conformidade: O Fortify WebInspect fornece descobertas técnicas detalhadas para desenvolvedores e relatórios de resumo para a gerência. Ele alinha as descobertas com os padrões e inclui relatórios de conformidade. Por ser frequentemente usado em setores regulamentados, ele oferece relatórios para satisfazer PCI DSS, DISA STIG, OWASP e outras diretrizes prontas para uso.
Nota: Após a aquisição da OpenText, o Fortify WebInspect agora faz parte do portfólio OpenText Cybersecurity. Às vezes, é referido apenas como “OpenText Testes Dinâmicos de Segurança de Aplicações (ou Testes de Segurança em Tempo de Execução) (DAST)”. O produto principal é o mesmo, continuando a tradição do WebInspect. Usuários notaram que o WebInspect pode ser intensivo em recursos e pode exigir ajustes para evitar sobrecarregar algumas aplicações, mas é muito eficaz na descoberta de problemas complexos.
6. Invicti
Netsparker (agora conhecido como Invicti) é um scanner automatizado líder de segurança de aplicações web para ambientes corporativos. O Netsparker foi renomeado para Invicti nos últimos anos, depois que a Invicti Security unificou os produtos Netsparker e Acunetix sob o mesmo teto. O Invicti (Netsparker) usa o Proof-Based Scanning com o objetivo de eliminar falsos positivos ao realmente confirmar vulnerabilidades. Também incorpora alguns elementos de teste interativos para uma análise mais aprofundada.
Principais recursos:
- Proof-Based Scanning: O Invicti tenta automaticamente confirmar vulnerabilidades explorando-as de forma segura. Por exemplo, se encontrar uma falha de injeção de SQL, ele executará um payload benigno que extrai uma amostra de dados para comprovar o problema. O objetivo é gastar menos tempo verificando manualmente os achados.
- Amplo Suporte Tecnológico: O Invicti pode escanear aplicações web tradicionais, SPAs com JavaScript intenso e todos os tipos de APIs (REST, SOAP, GraphQL, gRPC). Ele lida eficazmente com frameworks modernos e inclui suporte para escanear tecnologias corporativas (ele pode navegar por autenticações personalizadas, lidar com tokens OAuth, etc.). Também tem a capacidade de testar corpos de requisição JSON e envelopes SOAP para falhas de injeção.
- Capacidades Híbridas IAST: O Invicti combina DAST com IAST (Teste Interativo de Segurança de Aplicações) através de sua tecnologia de Agente. Se você puder implantar um agente leve junto com sua aplicação, o scanner pode instrumentar a aplicação durante a execução para obter insights adicionais (como confirmar a linha exata de código para uma vulnerabilidade). Essa abordagem híbrida pode aumentar a cobertura e o detalhe sem exigir acesso total ao código-fonte.
- CI/CD e Integração: O Invicti oferece plugins para pipelines de CI (Jenkins, Azure DevOps, GitLab CI, etc.), integração com gerenciamento de projetos e ticketing (Jira, Azure Boards) e conexão com WAFs para patching virtual instantâneo. Isso o torna adequado para fluxos de trabalho DevSecOps onde a varredura contínua é necessária.
- Escalabilidade e Gerenciamento: A plataforma pode escalar para escanear milhares de aplicações com agendamento, priorização e controle de acesso baseado em função para colaboração em equipe. O Invicti também oferece um dashboard multi-tenant e recursos de descoberta de ativos (ele pode descobrir novas aplicações web em seu ambiente para garantir que sejam escaneadas). É frequentemente usado como a espinha dorsal para o gerenciamento de vulnerabilidades de aplicações web corporativas.
Destaque da avaliação: “Invicti, que é Netsparker, me forneceu um grande banco de dados de vulnerabilidades para encontrar vulnerabilidades de execução remota, invalidação de domínio e muitos patches de vulnerabilidade... A varredura recorrente me permite buscar arquivos em um nível de integridade.” (Avaliação G2).
Em termos simples: os usuários apreciam a profundidade da cobertura de vulnerabilidades e a capacidade de agendar varreduras repetidas para detectar regressões. Alguns observam que a amplitude dos testes da Invicti (mais de 1400 testes únicos) é enorme, embora certas funcionalidades avançadas possam exigir ajustes finos.
7. Nikto

Nikto é um clássico scanner de servidor web de código aberto. É uma ferramenta simples, mas eficaz, que realiza verificações abrangentes para milhares de problemas potenciais em servidores web. Nikto é uma ferramenta de linha de comando baseada em Perl, mantida pela CIRT.net, e tem sido um item essencial na caixa de ferramentas de segurança por anos. Embora o Nikto não tenha a interface polida ou a lógica complexa de scanners modernos, é muito útil para identificar rapidamente vulnerabilidades conhecidas e configurações inseguras.
Principais recursos:
- Grande Banco de Dados de Verificações: Nikto pode testar mais de 7.000 arquivos/CGIs e configurações potencialmente perigosos em um servidor web. Isso inclui verificações de arquivos padrão (como páginas de administração, scripts de instalação), aplicativos de exemplo, backups de configuração (arquivos *.old, *.bak) e outros artefatos que os atacantes geralmente procuram. Ele também detecta versões desatualizadas de mais de 1.250 servidores e componentes de software, juntamente com problemas específicos de versão para mais de 270 produtos de servidor.
- Verificações de Configuração do Servidor: Nikto não apenas procura por vulnerabilidades de aplicativos web; ele examina informações do servidor. Por exemplo, ele reportará se a indexação de diretórios está habilitada, se métodos HTTP como PUT ou DELETE são permitidos (o que pode permitir o hacking de upload de arquivos), ou se certos cabeçalhos HTTP inseguros estão presentes/ausentes. É uma ótima auditoria rápida de hardening de servidor web.
- Fast and No-Frills: Nikto is not stealthy – it’s designed to run as fast as possible and will be noisy in logs. This is fine for authorized scanning. It’s command-line driven, so you can feed it a list of hosts or use it in scripts easily. Running nikto -h <hostname> will output a list of identified issues in plain text.
- Opções de Saída: Ele pode salvar resultados em múltiplos formatos (texto simples, XML, HTML, NBE, CSV, JSON), o que é útil se você quiser alimentar a saída em outras ferramentas ou sistemas de relatórios. Muitas pessoas usam Nikto como parte de um conjunto de ferramentas maior, analisando seus resultados para sinalizar certas descobertas.
- Extensibilidade: Embora não seja tão modular quanto alguns, você pode personalizar o comportamento do Nikto. Ele suporta plugins (seu banco de dados de verificações é essencialmente um conjunto de plugins). Você pode atualizar suas assinaturas, e ele é frequentemente atualizado pela comunidade com novas verificações. Além disso, ele suporta técnicas anti-IDS do LibWhisker se você tentar discrição (embora por padrão seja barulhento).
Dica profissional: Como o Nikto é passivo em termos de lógica (sem login, sem rastreamento pesado), ele é muito rápido. Você pode integrar o Nikto a um pipeline de CI para uma varredura rápida de cada build (para garantir, por exemplo, que nenhum endpoint de depuração tenha sido implantado acidentalmente). Embora possa relatar algumas descobertas de nível “info” que não são vulnerabilidades verdadeiras, ele oferece a tranquilidade de que você não deixou algo óbvio por aí.
8. OWASP ZAP
OWASP ZAP (Zed Attack Proxy) é uma ferramenta DAST gratuita e de código aberto mantida pelos líderes do projeto OWASP. É uma das ferramentas DAST mais populares devido ao seu custo (gratuito), comunidade aberta e rica funcionalidade. ZAP é tanto um proxy para testes manuais quanto um scanner automatizado. É frequentemente considerado a alternativa de código aberto ao Burp Suite para aqueles com orçamento limitado, e é uma opção fantástica para desenvolvedores e pequenas empresas começarem testes de segurança sem obstáculos de aquisição.
Principais recursos:
- Varredura Ativa e Passiva: O ZAP realiza varredura passiva observando o tráfego que passa por ele (via seu proxy ou addon spider) e sinalizando problemas, e varredura ativa onde ele injeta ataques ativamente assim que descobre páginas. O modo passivo é ótimo para um começo suave (não modificará nada, apenas observará coisas como vazamento de informações ou cabeçalhos de segurança), enquanto a varredura ativa encontrará os bugs reais (SQLi, XSS, etc.) atacando o aplicativo.
- Proxy e Ferramentas de Teste Manual: Assim como o Burp, o ZAP pode funcionar como um proxy interceptador. Ele também possui várias ferramentas: um proxy HTTP interceptador, um addon spider para rastrear conteúdo, um fuzzer para atacar entradas e um console de script (com suporte para escrever scripts em Python, Ruby, etc. para estender o ZAP). O modo Heads-Up Display (HUD) permite até mesmo sobrepor informações de varredura no seu navegador enquanto você navega – muito útil para desenvolvedores que estão aprendendo segurança.
- Automação e API: O ZAP foi construído com a automação em mente para integração de QA. Ele possui uma API poderosa (REST e uma API Java) que permite controlar todos os aspectos do ZAP. Muitas equipes usam a API do ZAP em pipelines de CI. Por exemplo, iniciar o ZAP no modo daemon, rastrear um alvo, executar uma varredura ativa e, em seguida, extrair os resultados – tudo automatizado. Existem até ações prontas do GitHub e plugins Jenkins para o ZAP. Isso o torna uma boa opção para DevSecOps com orçamento limitado.
- Extensibilidade via Add-ons: Como destacado anteriormente, o ZAP possui um marketplace de add-ons (o ZAP Marketplace) onde você pode instalar add-ons oficiais e da comunidade. Estes incluem regras de varredura especializadas (para JSON, XML, SOAP, WebSockets, etc.), integrações ou recursos de conveniência. A comunidade atualiza constantemente as regras de varredura, incluindo regras alpha/beta para tipos de vulnerabilidade emergentes. Isso mantém as capacidades de varredura do ZAP em evolução.
- Comunidade e Suporte: Sendo parte do OWASP, ele possui uma forte comunidade de usuários. Há muita documentação, vídeos de treinamento gratuitos e fóruns ativos. Embora você não obtenha suporte comercial (a menos que use consultores terceirizados), o conhecimento disponível muitas vezes rivaliza com o suporte do fornecedor. O ZAP também é atualizado regularmente por seus líderes de projeto e contribuidores.
Destaque da avaliação: “A ferramenta OWASP é gratuita, o que lhe confere uma grande vantagem, especialmente para empresas menores utilizarem a ferramenta.” peerspot.com. Esse sentimento é comum – o ZAP reduz a barreira de entrada para a segurança web.
Pode não ter recursos premium prontos para uso como alguns scanners comerciais, mas para muitos casos de uso, ele cumpre o trabalho de forma eficaz.
9. Qualys Web Application Scanner (WAS)
Qualys Web Application Scanning (WAS) é uma oferta DAST baseada em Cloud da Qualys, integrada à sua QualysGuard Security and Compliance Suite. O Qualys WAS aproveita a plataforma Cloud da Qualys para fornecer um serviço de varredura sob demanda para aplicações web e APIs. É particularmente atraente para empresas que já utilizam a Qualys para varredura de vulnerabilidades de rede ou conformidade, pois estende essa visão unificada para aplicações web. O Qualys WAS é conhecido por sua escalabilidade (varredura de milhares de sites) e sua facilidade de uso via modelo SaaS.
Principais recursos:
- Baseado em Cloud e Escalável: O Qualys WAS é entregue como um serviço que você executa a partir da Qualys Cloud contra seus alvos (com a opção de usar dispositivos de varredura distribuídos para aplicações internas). Isso significa nenhuma sobrecarga de manutenção para a própria ferramenta e a capacidade de executar muitas varreduras em paralelo. A plataforma descobriu e verificou mais de 370 mil aplicações web e APIs, mostrando seu uso generalizado.
- Ampla Cobertura de Vulnerabilidades: Ele detecta vulnerabilidades, incluindo Top 10 OWASP (SQLi, XSS, CSRF, etc.), configurações incorretas, exposição de dados sensíveis (por exemplo, números de cartão de crédito em páginas) e até mesmo infecção por malware em sites. Ele também verifica coisas como exposição inadvertida de PII (informações de identificação pessoal) ou Secrets em páginas web. A Qualys usa alguma IA/ML (machine learning) em sua varredura para melhorar a detecção de problemas complexos e reduzir falsos positivos (de acordo com o marketing deles).
- Teste de Segurança de API: O Qualys WAS também cobre o Top 10 de API OWASP. Ele pode importar arquivos OpenAPI/Swagger ou coleções Postman e testar APIs REST de forma abrangente. Ele monitora por "drift" (desvio) das especificações da API, o que significa que se sua implementação não corresponde ao arquivo Swagger (o que poderia indicar endpoints não documentados), a Qualys pode sinalizá-lo. Isso é ótimo para gerenciar a segurança de API.
- Integração e DevOps: A Qualys fornece uma API abrangente para todos os seus produtos, incluindo o WAS. Você pode automatizar varreduras, extrair relatórios e até mesmo integrar resultados em sistemas de rastreamento de defeitos. Eles também têm um plug-in do Chrome (Qualys Browser Recorder) para registrar sequências de autenticação ou fluxos de trabalho do usuário que podem ser carregados para o Qualys WAS para varredura das partes de uma aplicação que exigem login. Além disso, os resultados do Qualys WAS podem alimentar seu WAF (se você usa o Qualys WAF) para patching virtual rápido.
- Conformidade e Relatórios: Como a Qualys foca muito em conformidade, o WAS é capaz de gerar os relatórios necessários para atender ao PCI DSS 6.6 (requisito de varredura de vulnerabilidades de aplicações web) e outras políticas. Todos os achados são consolidados na interface Qualys, que pode ser compartilhada com outros módulos, como suas ferramentas de gerenciamento de vulnerabilidades ou gerenciamento de riscos. Esse relatório unificado é um ponto positivo para a gestão.
Nota da indústria: O Qualys WAS foi líder no GigaOm Radar de 2023 para Testes de Segurança de Aplicações. Usuários citam sua conveniência na Cloud e o benefício do monitoramento contínuo. Por outro lado, alguns acham a UI um pouco datada e a configuração inicial (como scripts de autenticação) com uma curva de aprendizado. Ainda assim, é uma escolha muito sólida com o apoio da Qualys.
10. Rapid7 InsightAppSec

Rapid7 InsightAppSec é uma solução DAST baseada na Cloud que faz parte da plataforma Insight da Rapid7. O InsightAppSec foca na facilidade de uso e integração, tornando os testes dinâmicos acessíveis tanto para equipes de segurança quanto para desenvolvedores. Ele aproveita a expertise que a Rapid7 possui (de produtos como Metasploit e suas ferramentas de gerenciamento de vulnerabilidades) para fornecer um scanner que pode lidar com aplicações web modernas, incluindo aplicações de página única e APIs. Como um serviço de Cloud, ele elimina a necessidade de gerenciar a infraestrutura do scanner.
Principais recursos:
- Cobertura de Aplicações Web Modernas: O InsightAppSec pode testar aplicações web tradicionais, bem como SPAs construídas em frameworks como React ou Angular. Ele tem a capacidade de executar JavaScript e rastrear conteúdo gerado dinamicamente. Também lida com HTML5 e padrões web mais recentes. A Rapid7 enfatiza que ele pode proteger tudo, desde formulários HTML legados até aplicações client-side modernas.
- Mais de 95 Tipos de Ataque: O scanner inclui mais de 95 tipos de ataque em seu repertório, cobrindo vetores comuns e complexos. Isso inclui os suspeitos usuais (SQLi, XSS) e também coisas como injeção CRLF, SSRF e outras falhas web menos comuns. Ele prioriza os achados com base no risco para ajudar você a focar no que realmente importa.
- UX Simplificada: O InsightAppSec é projetado com uma UI amigável. Configurar um scan é direto – forneça uma URL, informações de login opcionais e comece. A interface guia usuários menos experientes através da configuração. Uma vez que os scans são concluídos, os achados são explicados com conselhos de remediação e insights amigáveis para desenvolvedores. Ele também possui recursos como replay de ataque (para verificar um achado reproduzindo a requisição específica que o expôs).
- Escaneamento Paralelo e Sem Downtime: Por ser baseado na Cloud, você pode executar múltiplos scans simultaneamente sem se preocupar com recursos locais. Isso é ótimo para escanear múltiplos aplicativos ou para multitarefa (a Rapid7 observa que você pode escanear muitos alvos sem downtime do lado deles). Essa escalabilidade é útil para agências ou grandes organizações que escaneiam muitas aplicações web.
- Integração e Ecossistema: O InsightAppSec se integra à plataforma mais ampla Rapid7 Insight. Por exemplo, você pode enviar vulnerabilidades para o InsightVM (seu gerenciamento de vulnerabilidades) ou gerar tickets no Jira. Ele também pode se integrar a pipelines de CI e possui uma API para automação. Além disso, se você usa o Rapid7 InsightConnect (SOAR), pode automatizar ações DAST (como acionar um scan quando um novo aplicativo é implantado, etc.).
Destaque da avaliação: “Usamos a Rapid7 para nossos testes de vulnerabilidade e... Eles se mostraram inestimáveis ao fornecer uma solução completa e eficaz.”.
Os usuários frequentemente elogiam o suporte da Rapid7 e o polimento geral da plataforma. Um possível ponto negativo mencionado é que, às vezes, a correção de bugs no produto pode ser lenta, mas novos recursos e melhorias são lançados regularmente.
11. Tenable.io Web App Scanning
Tenable.io Web App Scanning é a oferta DAST dedicada da Tenable dentro de sua plataforma Tenable.io Cloud. A Tenable se posiciona como um scanner fácil de usar, porém abrangente, frequentemente atraindo clientes que já utilizam o Tenable.io para gerenciamento de vulnerabilidades.
Principais recursos:
- Plataforma Unificada: O Tenable.io WAS coexiste com outros serviços da Tenable (como Tenable.io Gerenciamento de Vulnerabilidades, segurança de contêineres, etc.), de modo que todos os resultados são acessíveis em um único dashboard. Para equipes de segurança, esta “visão unificada” para vulnerabilidades de infraestrutura e web é conveniente. Você pode ver as vulnerabilidades de suas aplicações web em contexto com as vulnerabilidades de rede, rastrear pontuações de risco de ativos e gerenciar tudo em conjunto.
- Facilidade de Implantação: Como um produto SaaS, você pode iniciar uma varredura com poucos cliques. É possível escanear aplicações web externas de forma imediata. Para aplicações internas, você pode implantar um appliance de scanner Tenable que realizará a varredura e reportará para a Cloud. A configuração é direta, e a Tenable oferece modelos para varreduras rápidas vs. varreduras profundas.
- Rastreamento e Auditoria Automatizados: O scanner rastreia automaticamente a aplicação para construir um mapa do site e então audita cada página/formulário que encontra. Ele testa pontos de injeção e vulnerabilidades comuns. A Tenable tem aprimorado o motor de varredura para lidar com aplicações web modernas (como processamento de JS). Embora não seja tão promovido no marketing quanto alguns concorrentes, na prática ele cobre a maioria das vulnerabilidades padrão e possui verificações específicas para itens como DOM XSS e ataques baseados em JSON.
- Resultados Rápidos e Varreduras Incrementais: O Tenable.io WAS enfatiza a entrega rápida de valor. Ele pode entregar resultados acionáveis em minutos para problemas comuns. Também é projetado para varredura contínua, o que é útil para ambientes de desenvolvimento ágil com lançamentos frequentes.
- Integração e DevOps: O Tenable.io possui uma API, para que você possa acionar varreduras de aplicações web programaticamente ou integrar com CI/CD. Existem também integrações para enviar descobertas para sistemas de tickets. Se estiver usando Infraestrutura como Código, você poderia até mesmo criar um ambiente de teste, escanear com Tenable.io WAS via API, e depois destruí-lo.
- Complementar ao Nessus: A Tenable frequentemente sugere usar Nessus e WAS juntos – Nessus para verificações de rede e web básicas, e WAS para testes mais aprofundados de aplicações web. Se você já gerencia varreduras do Nessus no Tenable.io, adicionar o WAS é contínuo. Os dashboards podem mostrar pontuações de risco combinadas, etc. Os recursos de análise da Tenable (com Tenable Lumin) podem então priorizar problemas em todos os tipos de ativos de forma consistente.
Observação: A Tenable tem investido em WAS para acompanhar os concorrentes; em 2024, eles adicionaram suporte para recursos como gravação de sequências de login de forma mais fácil e varredura aprimorada de aplicações de página única.
Usuários comentam que é “simples, escalável e automatizado” – alinhando-se com a mensagem da Tenable de fornecer DAST abrangente sem muitas complicações. É uma ferramenta “versátil”.
12. Wapiti
Wapiti é um scanner de vulnerabilidades web gratuito e open-source escrito em Python. O nome Wapiti vem de uma palavra nativa americana para alce – apropriado, pois é ágil e poderoso em seu domínio. O Wapiti funciona como um scanner “black-box”: ele não precisa de código-fonte; ele simplesmente realiza fuzzing em sua aplicação web através de requisições HTTP, muito parecido com um DAST típico. É uma ferramenta de linha de comando que é especialmente popular entre entusiastas de open-source e é conhecida por ser ativamente mantida (com atualizações recentes adicionando novos módulos de vulnerabilidade).
Principais recursos:
- Abordagem de Fuzzing Black-Box: O Wapiti rastreia a aplicação web alvo para encontrar URLs, formulários e entradas, e então lança ataques injetando payloads para testar vulnerabilidades. Ele cobre uma ampla gama de falhas de injeção: SQL injection (baseado em erro, booleano, tempo), XPath injection, cross-site scripting (refletido e armazenado), inclusão de arquivos (local e remoto), OS command injection, ataques XML External Entity (XXE), e muito mais. Essencialmente, se houver um campo de entrada, o Wapiti tentará quebrá-lo.
- Módulos para Diversas Vulnerabilidades: Conforme listado em seu site, os módulos do Wapiti lidam com tudo, desde vulnerabilidades web clássicas até verificações como CRLF injection, redirecionamentos abertos, SSRF via serviço externo (ele pode testar se SSRF é possível usando um site externo do Wapiti como um 'catcher'), detecção de HTTP PUT (para verificar se o WebDAV está habilitado), e até mesmo verificações de vulnerabilidades como Shellshock em scripts CGI. Essa amplitude é impressionante para uma ferramenta gratuita.
- Autenticação e Escopo: O Wapiti suporta varredura autenticada via vários métodos: Basic, Digest, NTLM e autenticação baseada em formulário (você pode fornecer credenciais ou um cookie). Ele também permite restringir o escopo. Por exemplo, você pode instruí-lo a permanecer dentro de um determinado domínio ou pasta, o que é útil para evitar atacar links de terceiros ou subdomínios que você não possui. Você também pode excluir URLs específicas, se necessário.
- Geração de Relatórios: Ele gera resultados em múltiplos formatos (HTML, XML, JSON, TXT, etc.). O relatório HTML é útil para uma visualização rápida, enquanto JSON é útil se você quiser analisar ou mesclar resultados programaticamente. Os relatórios listam cada vulnerabilidade encontrada com detalhes como a requisição HTTP que foi usada para explorá-la, o que é ótimo para desenvolvedores reproduzirem e corrigirem.
- Ease of Use and Maintenance: Wapiti is easy to install (available via pip) and run (wapiti -u <url> starts a scan). It’s quite fast and you can adjust the number of concurrent requests. Importantly, Wapiti is actively maintained – the latest release (as of mid-2024) added new features and vulnerabilities. The project maintainers keep it up-to-date as new exploits (like recent CVEs) arise, which addresses a common issue where open-source scanners fall behind. It being Python means it’s also easy to tweak if you’re so inclined.
Aprovação da comunidade: Wapiti pode não ser tão famoso quanto ZAP, mas os usuários que o descobrem frequentemente elogiam sua eficácia. É como uma joia escondida para fuzzing automatizado de aplicações web.
Por não vir com uma GUI, é menos intimidador de integrar para aqueles que se sentem confortáveis com CLI. Além disso, suas atualizações (como a adição de detecção de Log4Shell no final de 2021) mostram que ele se adapta a eventos de segurança significativos. Se você está montando um kit de ferramentas AppSec de código aberto, Wapiti + ZAP juntos cobrem uma vasta área.
As 5 Melhores Ferramentas DAST para Desenvolvedores
A maioria dos desenvolvedores não acorda animada para executar varreduras de segurança. Se você é um desenvolvedor lendo isso agora, sabe que é verdade. Você está aqui para entregar funcionalidades, não para lutar com ferramentas que o inundam com falsos positivos.
É por isso que as melhores ferramentas DAST para desenvolvedores são diferentes das ferramentas corporativas.
Ao escolher uma ferramenta DAST como desenvolvedor, considere:
- Integração com CI/CD e IDEs: A ferramenta se integra ao seu pipeline de build ou oferece um plugin de IDE? Testes de segurança automatizados em CI ajudam a identificar problemas antes do merge. Algumas plataformas (como a segurança CI/CD da Aikido) tornam isso contínuo.
- Baixos Falsos Positivos e Ruído: Desenvolvedores não têm tempo para perseguir fantasmas. Ferramentas que validam descobertas (por exemplo, Invicti) ou que possuem alta precisão são preferíveis, para que, quando um bug é sinalizado, valha a pena corrigi-lo.
- Saída Acionável: Procure por scanners que ofereçam conselhos claros de remediação ou até mesmo exemplos de código para corrigir o problema. Melhor ainda, algumas ferramentas focadas em desenvolvedores fornecem correções automatizadas ou pull requests (o AI Autofix da Aikido, por exemplo, pode gerar patches para certos problemas).
- Velocidade e Varreduras Sob Demanda: Em um ambiente de desenvolvimento, varreduras mais rápidas permitem feedback ágil. Ferramentas que podem escanear mudanças incrementais ou URLs específicas (em vez de todo o aplicativo a cada vez) ajudam a integrar-se ao ciclo de desenvolvimento iterativo.
- Custo (para indivíduos ou pequenas equipes): Opções gratuitas ou acessíveis são atraentes, especialmente em organizações sem um orçamento de segurança dedicado. Ferramentas de código aberto ou serviços com planos gratuitos se encaixam bem aqui.
A seguir estão as 5 melhores ferramentas DAST para desenvolvedores:
- Aikido Security – Tudo-em-Um Amigável ao Desenvolvedor
- OWASP ZAP – Código Aberto e Programável
- Burp Suite (Community/Pro) – Adjunto para Testes Manuais
- StackHawk – DAST Integrado ao CI/CD (Menção honrosa)
- Wapiti – Verificações CLI Rápidas
Por que estas: Essas ferramentas enfatizam a fácil integração, a imediatidade dos resultados e a acessibilidade. Elas permitem que os desenvolvedores “movam para a esquerda” na segurança – identificando e corrigindo vulnerabilidades durante o desenvolvimento, muito antes de o código chegar à produção.
Ao usá-las, os desenvolvedores podem melhorar iterativamente a segurança, assim como fazem com a qualidade do código com testes unitários. O aprendizado obtido ao interagir com essas ferramentas (especialmente as interativas como ZAP ou Burp) também aprimora os desenvolvedores na mentalidade de segurança, o que é um benefício oculto, mas valioso.
A tabela abaixo compara as ferramentas DAST mais adequadas para desenvolvedores que precisam de feedback rápido, fácil integração CI/CD e relatórios com pouco ruído.
As 6 Melhores Ferramentas DAST para Empresas
Empresas não têm apenas “alguns aplicativos”. Elas têm centenas, às vezes milhares, com cada um sendo um potencial ponto de entrada se não for verificado. Esse tipo de escala muda o jogo.
A ferramenta DAST certa não se trata apenas de encontrar vulnerabilidades. É sobre gerenciá-las em um portfólio extenso. Isso significa acesso baseado em função para diferentes equipes, relatórios prontos para conformidade para auditores e integrações com os sistemas que você já utiliza — como ticketing, governança e automação de fluxo de trabalho.
A seguir, são considerações para ferramentas DAST empresariais:
- Escalabilidade e Gerenciamento: A ferramenta deve ser capaz de escanear muitas aplicações (possivelmente de forma concorrente), com gerenciamento centralizado de agendamentos de varredura, resultados e permissões de usuário. Consoles empresariais ou ambientes multiusuário são importantes (por exemplo, HCL AppScan Enterprise ou plataforma Invicti).
- Integrações Empresariais: A integração com sistemas como SIEMs, plataformas GRC, rastreadores de defeitos (Jira, ServiceNow) e gerenciamento de identidade (suporte a SSO) é frequentemente necessária. Além disso, acesso via API para integração personalizada na cadeia de ferramentas DevSecOps da empresa.
- Conformidade e Relatórios: Empresas frequentemente precisam gerar documentação de conformidade. Ferramentas que podem produzir relatórios detalhados para PCI, SOC2, ISO27001, etc., e rastrear a conformidade com políticas ao longo do tempo agregam muito valor. A capacidade de categorizar ativos (por unidade de negócio, nível de risco, etc.) e obter análises (tendências, SLAs na remediação de vulnerabilidades) é útil para o gerenciamento.
- Suporte e Treinamento: Ter um fornecedor que oferece suporte robusto (engenheiros de suporte dedicados, serviços profissionais) e treinamento é um fator importante. Ferramentas empresariais vêm com SLAs para questões de suporte. Para ferramentas de código aberto, esta é uma lacuna, razão pela qual grandes empresas tendem a optar por soluções comerciais, apesar do custo.
- Cobertura Abrangente: Empresas não podem se dar ao luxo de deixar passar nada. A ferramenta deve idealmente cobrir não apenas vulnerabilidades web padrão, mas também aspectos como testes de lógica de negócios, ou fornecer maneiras de estender os testes. Algumas empresas usam múltiplas ferramentas DAST para cobrir lacunas – mas uma única ferramenta robusta é preferível para maior eficiência.
A seguir, as 6 melhores ferramentas DAST para empresas:
- Invicti (Netsparker) – Precisão e Escala
- HCL AppScan (Standard/Enterprise) – Poder Legado Empresarial
- Micro Focus Fortify WebInspect – Integração Profunda com SDLC
- Qualys WAS – Escala Cloud e Descoberta de Ativos
- Tenable.io WAS – Gerenciamento Unificado de Riscos
- Aikido Security – Plataforma DevSecOps Empresarial
Por que estes: Eles atendem aos requisitos empresariais de escala, suporte e integração. Em grandes organizações, uma ferramenta DAST que pode escanear 500 aplicativos e, em seguida, gerar um relatório executivo mostrando “reduzimos a contagem de vulnerabilidades do Top 10 OWASP em 20% neste trimestre” é ouro. Ferramentas como Invicti, Qualys, etc., fornecem esses tipos de métricas e consolidações. Além disso, empresas frequentemente precisam escanear aplicativos internos atrás de firewalls – ferramentas com mecanismos de varredura on-premise (como scanners Qualys ou instalações WebInspect no local) são necessárias, e todas as opções acima as fornecem.
As 4 Melhores Ferramentas DAST para Startups
Startups se movem rapidamente. Essa é a vantagem — mas também é o risco. Com equipes pequenas e orçamentos mais apertados, a segurança frequentemente é deixada de lado até que um cliente, investidor ou uma lista de verificação de conformidade force a discussão.
A boa notícia? Você não precisa de uma equipe AppSec de 20 pessoas ou um investimento de porte empresarial para construir uma base de segurança sólida.
Principais necessidades para startups em uma ferramenta DAST:
- Custo-benefício: Soluções gratuitas ou de baixo custo, ou ferramentas com planos gratuitos que cobrem aplicativos pequenos, são ideais. Startups também podem considerar o código aberto para evitar custos recorrentes.
- Simplicidade: Pode não haver um engenheiro de segurança dedicado, então desenvolvedores ou DevOps executarão as varreduras. A ferramenta deve ser fácil de configurar (SaaS preferível para evitar infraestrutura) e fácil de interpretar.
- Ganhos Rápidos: Startups se beneficiam de ferramentas que encontram os problemas mais críticos rapidamente (por exemplo, configurações incorretas comuns, vulnerabilidades evidentes) – essencialmente uma verificação de sanidade. Elas podem não precisar do scanner mais exaustivo; algo para identificar os itens de alto risco geralmente é suficiente no início.
- Integração com o Workflow de Desenvolvimento: Startups frequentemente possuem desenvolvimento moderno e ágil. Ferramentas que se integram com GitHub Actions ou similares podem ajudar a automatizar a segurança sem processos pesados.
- Escalabilidade (preparação para o futuro): Embora não seja um requisito principal, uma ferramenta que possa crescer com eles (mais aplicativos, mais varreduras) é um bônus, para que não precisem trocar de ferramentas à medida que escalam. Mas, no início, o custo pode se sobrepor a isso.
As 4 melhores ferramentas DAST para startups são as seguintes:
- OWASP ZAP – Gratuito e Confiável
- Aikido Security – Plano Gratuito e Tudo em Um
- Acunetix (da Invicti) – Opção Amigável para PMEs
- Burp Suite Community – Aprendizado e Exploração Manual
Por que estas: Elas não custam nada ou se encaixam facilmente no orçamento de uma startup, e não exigem um especialista em tempo integral para operar. O objetivo para uma startup é evitar ser um alvo fácil para atacantes. Executar essas ferramentas pode identificar os problemas evidentes (credenciais padrão, endpoints de administração abertos, injeções SQL, etc.) e aumentar drasticamente a postura de segurança com investimento mínimo.
Além disso, demonstrar que você utiliza ferramentas reconhecidas como o OWASP ZAP pode aumentar a confiança quando aquele inevitável questionário de segurança vier de um cliente em potencial.
As 4 Melhores Ferramentas DAST Gratuitas
Qualquer pessoa que busca melhorar a segurança de seus aplicativos web sem gastar dinheiro se sentiria atraída por essas ferramentas. Isso inclui desenvolvedores amadores, estudantes, pequenas organizações ou até mesmo empresas maiores que estão experimentando antes de adquirir uma solução.
“Gratuito” neste contexto pode significar completamente de código aberto ou versões gratuitas de produtos comerciais.
Opções gratuitas de DAST geralmente apresentam algumas limitações (seja em recursos, suporte ou profundidade de varredura), mas oferecem um valor incrível para necessidades básicas.
Critérios/características para as melhores ferramentas gratuitas:
- Sem Custo, Sem Compromisso: Verdadeiramente gratuito para usar (não apenas um teste curto). Idealmente de código aberto ou com suporte da comunidade.
- Eficácia: Mesmo que gratuita, a ferramenta deve encontrar um número significativo de vulnerabilidades. A linha de base é cobrir as questões do Top 10 OWASP.
- Suporte da Comunidade: Ferramentas gratuitas frequentemente dependem de fóruns da comunidade, documentação e atualizações. Uma comunidade vibrante garante que a ferramenta permaneça útil.
- Facilidade de Uso vs. Curva de Aprendizagem: Algumas ferramentas gratuitas são prontas para uso, enquanto outras exigem habilidade. Listaremos uma variedade: algumas que “apenas funcionam” e outras que podem exigir mais expertise (para aqueles dispostos a investir tempo em vez de dinheiro).
A seguir estão as 4 melhores ferramentas DAST gratuitas:
- OWASP ZAP
- Nikto
- Wapiti
- Burp Suite Community Edition
Nota: Muitos players comerciais oferecem testes gratuitos (como 14 dias de teste do Acunetix ou uma varredura gratuita limitada da Qualys, etc.), mas essas não são soluções sustentáveis. Assim, me atenho a ferramentas que são gratuitas a longo prazo, não limitadas por tempo.
Por que estes: Eles cobrem o básico (e mais) sem qualquer barreira financeira. Ferramentas gratuitas são cruciais para democratizar a segurança – elas permitem que qualquer pessoa teste suas aplicações. Empresas com orçamento zero ainda podem melhorar sua postura de segurança usando-as.
É frequentemente recomendado executar várias ferramentas gratuitas em combinação, pois cada uma pode detectar coisas que as outras perdem. Por exemplo, execute Nikto + ZAP + Wapiti juntos – se todos os três concordarem que um aplicativo está “limpo”, você provavelmente lidou com os problemas óbvios. Tudo isso sem gastar um centavo.
As 4 Melhores Ferramentas DAST de Código Aberto
Isso interessará a entusiastas de segurança e organizações comprometidas com soluções de código aberto, ou àqueles que desejam total transparência e controle sobre a ferramenta. Ferramentas de código aberto também são favorecidas por instituições de ensino e por empresas com regras de aquisição rigorosas que preferem software auditado pela comunidade.
“Código aberto” se sobrepõe a “gratuito”, mas aqui nos referimos especificamente a ferramentas cujo código-fonte está disponível e que são tipicamente mantidas por uma comunidade (muitas vezes sob a OWASP ou organizações similares). O benefício é que você pode auditar o código do scanner, personalizá-lo e confiar que não há comportamento de caixa preta oculto.
A seguir estão as principais ferramentas DAST de código aberto (com um pouco de repetição do que foi dito acima):
- OWASP ZAP
- Wapiti
- Nikto
- Comunidade de Add-ons do OWASP ZAP (menção honrosa)
Por que código aberto? Segurança é sobre confiança. Com DAST de código aberto, você pode inspecionar exatamente quais testes estão sendo realizados e como os dados são tratados (importante se estiver varrendo aplicativos sensíveis – você sabe que a ferramenta não está desviando dados, por exemplo, porque você pode ver o código). Isso também significa que, se a ferramenta não se encaixar perfeitamente nas suas necessidades, você tem o poder de alterá-la. Organizações que estão dispostas a investir esforço de engenharia em vez de dinheiro podem construir soluções DAST muito personalizadas a partir desses projetos.
As 6 Melhores Ferramentas DAST para DevSecOps
DevSecOps é a prática de integrar verificações de segurança em pipelines de integração contínua e entrega contínua, com um alto grau de automação e colaboração entre dev, sec e ops. Essas equipes buscam ferramentas que possam operar de forma autônoma, produzir saída legível por máquina e, talvez, barrar builds com base em critérios de segurança. Elas também frequentemente preferem ferramentas que possam ser “deslocadas para a esquerda” (usadas precocemente pelos desenvolvedores), bem como continuamente em pós-produção.
Fatores importantes para DAST em DevSecOps:
- Integração CI/CD: A ferramenta deve ter uma CLI ou API REST e, idealmente, plugins para sistemas CI populares (Jenkins, GitLab CI, GitHub Actions, Azure DevOps, etc.). Deve ser fácil de iniciar como parte de um pipeline (versões Containerizadas ajudam aqui).
- Saída Amigável à Automação: Resultados em formatos como JSON ou SARIF que podem ser consumidos por outros sistemas para tomada de decisão automatizada. Por exemplo, interrompa a build se novas vulnerabilidades de alta gravidade forem encontradas – isso requer a análise automática da saída do scanner.
- Scans Incrementais ou Rápidos: Scans DAST completos podem ser lentos, o que é um desafio para CI. Ferramentas que oferecem modos mais rápidos ou permitem direcionar componentes específicos (talvez via tagging de endpoints importantes) são úteis. Outra abordagem é a integração com suites de teste – por exemplo, atacando o aplicativo enquanto os testes de integração são executados (algumas configurações avançadas fazem isso).
- Flexibilidade de Ambiente: DevSecOps pode provisionar ambientes de teste efêmeros (por exemplo, implantar um branch de um aplicativo em um servidor de teste, escaneá-lo e depois desativá-lo). Ferramentas DAST que podem facilmente apontar para URLs dinâmicas e lidar com ambientes em constante mudança sem muita configuração manual se destacam aqui.
- Loops de Feedback: Um ideal de DevSecOps é o feedback imediato aos desenvolvedores. Assim, uma ferramenta DAST que pode comentar em um pull request, abrir tickets automaticamente ou enviar notificações no chat com os resultados, fomenta essa cultura de feedback rápido.
As principais ferramentas / abordagens para DevSecOps:
- Aikido Security – Automação de Pipeline
- OWASP ZAP (Dockerizado) – A Ferramenta Essencial do DevOps
- StackHawk – Desenvolvido especificamente para CI
- Invicti/Acunetix – plugins de CI
- Burp Suite Enterprise – Integração de Pipeline
- Tenable.io WAS – Cloud hooks
Em resumo, a automação é fundamental aqui. Ferramentas que não foram criadas para automação ainda podem ser usadas em pipelines (através de scripts criativos), mas aquelas que reconhecem o DevSecOps com recursos e integrações economizarão tempo. As opções acima são inerentemente amigáveis à automação (ZAP, Aikido, StackHawk) ou evoluíram para suportá-la devido à demanda do mercado (Invicti, Burp Enterprise).
Equipes DevSecOps também frequentemente usam múltiplos estágios de DAST: uma varredura rápida e leve em CI (para detectar problemas óbvios em minutos) e uma varredura mais profunda pós-implantação (que pode levar mais tempo, mas não bloqueia os desenvolvedores). As ferramentas escolhidas precisam suportar essa estratégia.
As 6 Melhores Ferramentas DAST para segurança de API
Público-alvo: Equipes que precisam testar especificamente APIs web (REST, SOAP, GraphQL) em busca de vulnerabilidades. Isso inclui desenvolvedores backend, engenheiros de plataforma de API e testadores de segurança focados em microsserviços. O teste de segurança de API é ligeiramente diferente do teste de UI web – não há interface de navegador, então você precisa de ferramentas que possam analisar esquemas de API, lidar com payloads JSON/XML e entender coisas como tokens de autenticação e chamadas de API multi-etapas.
Principais capacidades para DAST focado em API:
- Importação de Especificação de API: A ferramenta deve importar coleções Swagger/OpenAPI ou Postman para saber quais endpoints existem e seus formatos. Isso economiza tempo e garante a cobertura de todos os endpoints da API, mesmo aqueles que não são facilmente descobertos.
- Suporte a GraphQL: APIs GraphQL são agora comuns; testá-las requer tratamento especial (consultas de introspecção, consultas aninhadas). Um bom DAST de API deve ter módulos para GraphQL (por exemplo, verificando vulnerabilidades específicas de GraphQL como negação de serviço por consulta profundamente aninhada).
- Suporte a SOAP e APIs Legadas: Ainda relevante em empresas – ferramentas que podem testar serviços SOAP importando WSDL ou gravando chamadas SOAP. Além disso, o tratamento de coisas como gRPC pode ser considerado (embora o suporte DAST para gRPC ainda seja nascente; algumas ferramentas convertem gRPC para testes semelhantes a REST via proxies).
- Autenticação e Tokens: O teste de API precisa lidar com chaves de API, tokens OAuth, JWTs, etc. A ferramenta deve facilitar o fornecimento desses (talvez via um arquivo de configuração ou script de login) para que possa testar endpoints autorizados. É um bônus se também puder testar a lógica de autorização, por exemplo, IDOR (Insecure Direct Object References) manipulando IDs.
- Gerenciamento de Respostas Não-HTML: APIs retornam JSON ou XML. O scanner não deve esperar páginas HTML; ele deve analisar JSON e ainda encontrar problemas (como XSS em contexto JSON, ou erros SQL em respostas de API). Alguns scanners mais antigos só analisam respostas HTML, o que não é suficiente para APIs.
- Consciência de Rate Limiting: Atingir APIs com muita intensidade pode acionar Rate limiting ou até mesmo bloquear IPs. Scanners focados em API podem incluir configurações para respeitar Rate limiting ou limitar adequadamente, para evitar a interrupção do serviço (importante ao testar APIs em produção).
As seguintes são as principais ferramentas DAST para segurança de API:
- Invicti (e Acunetix) – descoberta de API e Testes
- Qualys WAS – suporte a API e OpenAPI v3
- OWASP ZAP – Com Add-ons para APIs
- Burp Suite – Ótimo para Testes Manuais de API
- Postman + Security Collections – (Aumentando o DAST)
- Aikido Security – Scanning de API integrado
Por que estes: Endpoints de API frequentemente contêm dados sensíveis e são propensos a problemas como bypass de autenticação, exposição excessiva de dados, etc. Ferramentas DAST tradicionais historicamente focavam em páginas web, mas as listadas acompanharam a tendência API-first. Usá-las garante que suas APIs de backend sejam tão testadas quanto seu front-end.
Dado o número de violações que agora envolvem APIs (lembre-se do vazamento de dados de usuários do Facebook via uma API, ou dos problemas de API da T-Mobile), focar na segurança de API é crítico. Ferramentas que podem simular consumo malicioso de API são a forma de descobrir essas falhas.
As 6 Melhores Ferramentas DAST para Aplicações Web
Isso pode parecer abrangente (já que a maioria dos DAST é para aplicações web), mas aqui interpretamos como organizações especificamente focadas em testar aplicações web tradicionais (websites, portais, sites de e-commerce) – possivelmente aquelas com interfaces de usuário ricas. Elas querem as ferramentas que melhor se desempenham na descoberta de vulnerabilidades de aplicações web nesses ambientes. Esta categoria basicamente pergunta: se sua principal preocupação é proteger aplicações web (com navegadores, formulários, contas de usuário, etc.), quais ferramentas são as mais eficazes no geral?
Aspectos importantes para o scanning de aplicações web puras (em oposição a APIs ou outros nichos):
- Rastreamento e Cobertura: Um scanner de aplicativos web deve rastrear efetivamente todos os links, incluindo aqueles gerados por scripts ou eventos do usuário. Ferramentas com algoritmos de rastreamento melhores (navegador headless, tratamento de SPAs) cobrirão uma maior parte do aplicativo.
- Gerenciamento de Sessão: Aplicações web frequentemente possuem login e estado complexos (carrinho de compras, fluxos de trabalho multi-etapas). As melhores ferramentas DAST para aplicações web podem lidar com isso via macros gravadas ou lógica de script.
- Profundidade da Vulnerabilidade: Para aplicações web, itens como XSS, SQLi, CSRF, inclusão de arquivos, etc., são cruciais. Algumas ferramentas possuem verificações mais abrangentes para XSS (refletido, armazenado, baseado em DOM) do que outras, por exemplo. A capacidade de uma ferramenta de encontrar XSS armazenado (que pode envolver uma página para submeter, outra para disparar) pode diferenciar as excelentes das boas.
- Tratamento de Falsos Positivos: Em uma aplicação web grande, você pode ter centenas de achados – ferramentas que verificam ou priorizam claramente a explorabilidade ajudam a focar em problemas reais.
- Verificações de Segurança do Lado do Cliente: Aplicações web modernas podem apresentar problemas como uso inseguro de armazenamento do lado do cliente, ou vulnerabilidades em scripts de terceiros. Algumas ferramentas DAST agora sinalizam se seu site está carregando um script com vulnerabilidade conhecida ou se a Content Security Policy está ausente. Estas são verificações mais “específicas para aplicações web”, indo além das vulnerabilidades brutas.
As principais ferramentas DAST para Aplicações Web:
- Aikido Security
- Invicti (Netsparker)
- Burp Suite Pro
- Acunetix
- OWASP ZAP
- HCL AppScan Standard
Por que estes: Eles oferecem a melhor chance de encontrar uma ampla variedade de vulnerabilidades em aplicações web típicas. Uma aplicação web pode ser algo extenso com várias funcionalidades; essas ferramentas são comprovadas no scanning de websites inteiros de ponta a ponta.
Ferramentas como Invicti e Burp são frequentemente usadas em conjunto: uma para amplitude, outra para profundidade. Acunetix ou AppScan, nas mãos de um analista, fornecem uma abordagem estruturada para o scanning que muitas equipes de segurança confiam para suas avaliações regulares de aplicações web corporativas. E o ZAP, sendo open source, democratiza essa capacidade.
Em suma, se seu objetivo é “Tenho este portal web, quero encontrar o máximo de problemas de segurança possível nele”, as ferramentas acima estão entre as primeiras que você consideraria.
As 6 Melhores Ferramentas DAST para APIs REST
Este é um foco mais restrito em APIs RESTful (que poderia ser considerado um subconjunto da segurança de API mencionada acima, mas aqui especificamente REST). Essas ferramentas são para equipes que desenvolvem APIs REST (JSON sobre HTTP, design stateless), incluindo backends de aplicativos móveis ou backends de SPA, que querem garantir que essas APIs não sejam vulneráveis.
Áreas de foco para DAST de API REST:
- Integração Swagger/OpenAPI: Muito importante para REST. Ferramentas que podem ingerir uma especificação Swagger para uma API REST podem enumerar todos os endpoints, métodos e parâmetros esperados, tornando a varredura mais eficaz.
- Vulnerabilidades específicas de REST: Testando coisas como tratamento inadequado de verbos HTTP (por exemplo, confusão entre GET e POST), falta de rate limiting, e configurações incorretas típicas de REST (como HTTP PUT permitido onde não deveria, ou métodos que deveriam ser idempotentes mas não são).
- Parameter fuzzing: REST endpoints often take JSON bodies. The scanner should try fuzzing JSON parameters with injection payloads, nested JSON objects, etc. Also, testing query parameters in URLs for REST endpoints (like /users?filter=<script>).
- Autenticação/Autorização: Muitas APIs REST usam tokens (Bearer tokens). As ferramentas precisam lidar com a anexação desses tokens a cada requisição. Além disso, testar a autorização (authZ) em REST (como alterar um ID na URL para o ID de outro usuário) é algo que algumas ferramentas DAST tentam (embora o teste de lógica de autorização verdadeira possa ir além do DAST).
- CSRF em APIs: Muitos pensam que as APIs não são afetadas por CSRF se não usarem cookies para autenticação, mas algumas usam (ou algumas permitem tanto cookies quanto tokens). Scanners poderiam verificar se endpoints que alteram o estado possuem proteções contra CSRF quando cookies são utilizados, por exemplo.
As 6 principais ferramentas para DAST de API REST:
- OWASP ZAP com Add-on OpenAPI
- Sinergia Postman + OWASP ZAP
- Invicti/Acunetix
- Burp Suite Pro
- Wapiti
- Tenable.io WAS
Por que estas: APIs REST estão por toda parte (qualquer aplicativo web/mobile moderno possui uma). Injeções em APIs REST podem ser tão devastadoras quanto em um formulário web. As ferramentas acima possuem capacidades comprovadas em testar REST especificamente. Como evidência, muitas ferramentas agora se alinham com OWASP API Security Top 10 – que é fortemente focado em REST.
Ferramentas como Invicti e Qualys WAS mencionam explicitamente a cobertura desses (como BOLA – Broken Object Level Authorization – que é o #1 no API Top 10, alguns scanners tentam detectar por fuzzing de ID).
Usar essas ferramentas em APIs REST ajuda a identificar problemas que a análise estática de código pode não detectar (especialmente problemas de configuração ou erros no controle de acesso). Elas simulam chamadas de clientes reais, que é a forma como os atacantes abordam as APIs.
Melhores 6 Ferramentas DAST para Aplicativos Móveis
Quando falamos sobre aplicativos móveis no contexto de DAST, estamos principalmente preocupados com os serviços de backend com os quais os aplicativos móveis se comunicam, bem como quaisquer webviews ou navegadores incorporados no aplicativo móvel.
A segurança binária pura de aplicativos móveis (como verificar o APK em busca de chaves hardcoded) é um domínio diferente (SAST móvel talvez), mas DAST para mobile significa testar as interfaces server-side do aplicativo móvel e, possivelmente, a comunicação de rede. O público pode ser de desenvolvedores móveis ou testadores de segurança garantindo que a interação cliente-servidor móvel seja segura.
Principais aspectos:
- Testando endpoints de API usados por dispositivos móveis: Muitas aplicações móveis usam APIs REST/GraphQL – o que nos remete à varredura de API. No entanto, a diferença é que você pode não ter documentação para estas se for uma API interna. Então, interceptar o tráfego móvel é o primeiro passo.
- Gerenciamento de fluxos de autenticação: Aplicativos móveis podem usar fluxos OAuth, ou autenticação personalizada com tokens. Uma ferramenta DAST para mobile precisa capturar e reutilizar esses tokens. Frequentemente, a maneira mais fácil é fazer proxy do aplicativo móvel e capturar uma sessão autenticada.
- Testando webviews: Algumas aplicações móveis são híbridas ou possuem componentes webview. Estes podem ser testados como aplicações web normais se você conseguir as URLs. Por exemplo, um aplicativo bancário pode ter uma seção de FAQ que é basicamente um webview de uma página web – isso deve ser escaneado para XSS, etc., porque se vulnerável, pode ser um vetor de ataque através do aplicativo.
- Verificação de protocolos inseguros: Um DAST que examina o tráfego móvel pode notar se o aplicativo chama uma URL HTTP em vez de HTTPS, ou aceita certificados SSL inválidos (algumas ferramentas podem testar por MITM com um certificado inválido para ver se o aplicativo ainda se conecta).
- Workflows e estado: Algumas interações móveis são sequências com estado (adicionar item ao carrinho, depois comprar). Simular isso pode exigir roteirizar o aplicativo móvel ou replicar as chamadas via um script automatizado. Isso é complexo, então ferramentas que podem gravar e reproduzir tais sequências ajudam.
As 6 Principais Ferramentas/Métodos para DAST de Aplicativos Móveis:
- Burp Suite – Padrão de Teste Móvel
- OWASP ZAP – Proxy e Varredura Móvel
- HCL AppScan com Analisador Móvel
- Aikido Security – Plataforma AppSec Completa (Mobile incluído)
- Postman para Mobile API + ZAP
- Nessus / Nexpose etc. – verificações de ambiente
Por que estes: Aplicativos móveis introduzem desafios únicos como certificate pinning, o que pode dificultar o DAST. Mas as abordagens acima são o que os profissionais de segurança usam para entrar na conversa entre o aplicativo móvel e o servidor.
Burp Suite é basicamente a ferramenta de fato para pentesting de aplicativos móveis devido à sua flexibilidade. O ZAP pode alcançar muito do mesmo com um pouco mais de configuração, mas sem custo. Estes permitem que você encontre problemas como:
A API confia em IDs fornecidos pelo usuário (levando à exposição de dados)?
O aplicativo móvel falha ao validar SSL (permitindo man-in-the-middle)?
Existem endpoints ocultos que o aplicativo chama e que não são óbvios?
Ao usar DAST em backends móveis, pode-se simular o que um invasor faria se desmontasse o aplicativo móvel e começasse a enviar requisições de API manipuladas. Isso é crítico; muitas violações móveis (pense no vazamento da API do Uber ou nos problemas passados da API do Snapchat) vêm de alguém que faz engenharia reversa do aplicativo móvel e abusa da API. Ferramentas DAST aplicadas das formas acima podem frequentemente detectar essas fraquezas antes que um invasor o faça.
Conclusão
A segurança de aplicações web em 2025 exige uma abordagem proativa – os atacantes estão constantemente sondando nossos websites, APIs e aplicativos móveis em busca de fraquezas. As ferramentas de Testes Dinâmicos de Segurança de Aplicações (DAST) são a pedra angular dessa defesa proativa, oferecendo uma visão de hacker das vulnerabilidades da sua aplicação. Ao simular ataques dinamicamente, as ferramentas DAST ajudam a identificar e corrigir problemas que as revisões de código estático podem ignorar, desde injeções SQL em um formulário esquecido até servidores mal configurados que aceitam cifras fracas.
Pronto para levar a segurança da sua aplicação para o próximo nível? Comece Gratuitamente com a plataforma all-in-one da Aikido.
Você também pode gostar:
- Melhores Scanners de API – Complemente o DAST com testes aprofundados específicos de API.
- As 7 Melhores Ferramentas ASPM – Orquestre os resultados de DAST em todo o SDLC.
- Melhores Ferramentas Automatizadas de Teste de Penetração – Automatize ainda mais com cobertura de nível pentest.



