Introdução
Equipes de software modernas têm um buffet de ferramentas de segurança para escolher. Veracode, Checkmarx e Fortify são três plataformas de segurança de aplicações de peso, frequentemente consideradas por líderes técnicos. Cada uma promete proteger seu código e detectar vulnerabilidades precocemente. Mas escolher a ferramenta certa importa: isso impacta o fluxo de trabalho do desenvolvedor, a cobertura de segurança e quanto tempo sua equipe gasta perseguindo falsos alarmes. Nesta comparação, detalharemos onde cada ferramenta se destaca, onde elas ficam aquém e por que a alternativa – Aikido Security – pode simplesmente oferecer uma maneira melhor de entregar código seguro sem as dores de cabeça habituais.
TL;DR
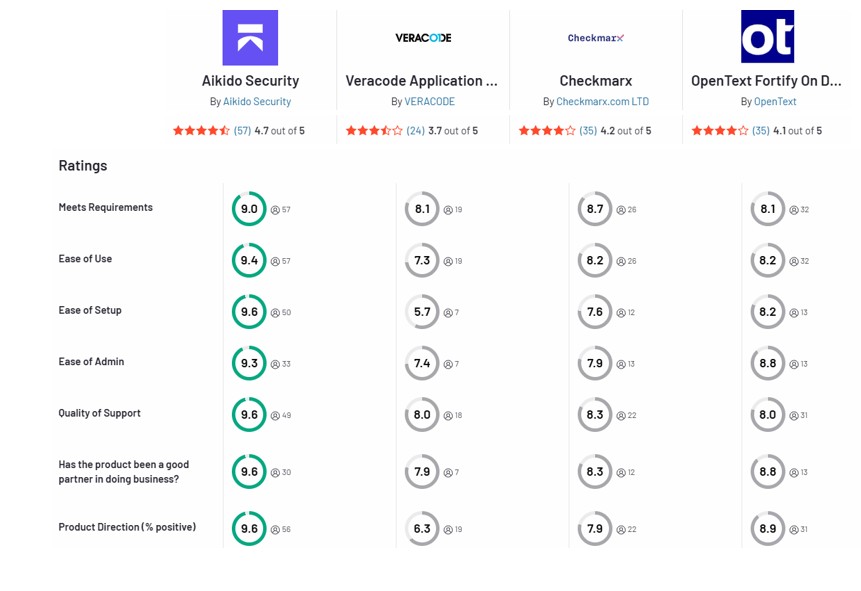
Veracode, Checkmarx e Fortify ajudam a proteger sua base de código, mas cada um tem seus pontos cegos. Veracode oferece um amplo kit de ferramentas de segurança (SAST, DAST, SCA) com foco em conformidade empresarial, mas é apenas na Cloud e pode ser lento. Checkmarx fornece análise estática amigável para desenvolvedores (sem necessidade de build) e implantação flexível, mas perde algumas camadas como runtime e Secrets. Fortify é um veterano on-premise conhecido por sua varredura profunda de código, mas é pesado – propenso a ruídos e exige manutenção séria. Aikido Security reúne todos esses mundos em uma única plataforma – cobrindo código, open-source, Cloud e Container – com muito menos falsos positivos e integração mais fluida. É a escolha prática para equipes de desenvolvimento modernas que desejam segurança sem complicação.
Visão Geral de Cada Ferramenta
Veracode
Veracode é uma plataforma de segurança de aplicações baseada em Cloud projetada para as necessidades empresariais. Ela realiza Testes de segurança de aplicações estáticas (SAST) analisando binários compilados em vez de código-fonte bruto. Essa abordagem significa que você faz upload da sua aplicação compilada para a Cloud da Veracode para varredura. O pacote da Veracode se expandiu para incluir varredura dinâmica (DAST) e análise de composição de software (SCA para bibliotecas open-source). A plataforma enfatiza a conformidade com políticas de segurança e governança, tornando-a popular entre as equipes de segurança em grandes organizações. Em resumo, a Veracode cobre uma ampla gama de testes e suporta muitas linguagens, mas como um SaaS totalmente gerenciado, exige o envio de código para a Cloud deles e pode parecer mais orientada à supervisão de segurança da informação do que à conveniência do desenvolvedor.
Checkmarx
Checkmarx é uma plataforma de segurança de aplicações focada em análise estática de código. Ao contrário da Veracode, a Checkmarx faz a varredura do seu código-fonte diretamente sem a necessidade de um build completo. Isso torna conveniente identificar problemas cedo e com frequência – os desenvolvedores podem executar varreduras durante o desenvolvimento ou em pipelines de CI sem empacotar a aplicação. A Checkmarx começou com SAST e depois adicionou seu próprio SCA para dependências, além de recursos mais recentes como infraestrutura como código e varredura de Container. Ela oferece opções de implantação on-premises e Cloud (SaaS), dando às equipes flexibilidade sobre onde as varreduras são executadas. A ferramenta é conhecida por ser amigável para desenvolvedores, com plugins IDE e integrações com GitHub/GitLab, Jenkins e outras ferramentas de desenvolvimento para um fluxo de trabalho mais fluido. No geral, a Checkmarx se posiciona como uma solução AST centrada no desenvolvedor que se encaixa em pipelines de DevOps, embora historicamente não tivesse um scanner dinâmico integrado (eles começaram a abordar essa lacuna).
Fortify
Fortify (agora sob OpenText, anteriormente Micro Focus/HPE Fortify) é uma suíte SAST empresarial de longa data. Ela fornece análise estática profunda através do Fortify Static Code Analyzer, tipicamente executado on-premises pelo cliente. Fortify faz a varredura do código-fonte (ou binários após uma etapa de build) para encontrar vulnerabilidades com um conjunto abrangente de regras. Tem sido um líder no Quadrante Mágico por mais de uma década, conhecido por sua cobertura muito completa de problemas de segurança. Fortify também oferece um componente de teste dinâmico (WebInspect) e pode integrar varredura de vulnerabilidades open-source via add-ons (por exemplo, um módulo SCA "Debricked") para uma cobertura de segurança mais completa. A plataforma suporta uma ampla gama de linguagens e frameworks, adequada para aplicações legadas e modernas. No entanto, Fortify é frequentemente descrito como pesado – pode exigir infraestrutura dedicada e até mesmo uma equipe para gerenciar varreduras e triar resultados. Um benefício dessa maturidade são os recursos empresariais robustos e relatórios. Em resumo, Fortify é uma poderosa solução de segurança de aplicações completa com ênfase on-prem, embora sua idade se reflita em uma experiência de usuário mais complexa e na necessidade de controlar falsos positivos.
(Agora vamos nos aprofundar em como essas ferramentas se comparam em relação aos fatores-chave que os líderes de tecnologia valorizam.)
Recursos Essenciais de Segurança
Abordagem e Tipos de Varredura: Todas as três ferramentas realizam análise estática (SAST) para identificar vulnerabilidades de codificação, mas suas abordagens diferem. A Veracode usa uma abordagem de SAST binário – você faz upload do código compilado e ela analisa os binários. Isso pode encontrar problemas em toda a aplicação (incluindo bibliotecas vinculadas) e, às vezes, identifica coisas que a análise em nível de código-fonte pode perder. A desvantagem é a velocidade: as varreduras binárias são frequentemente mais lentas e dificultam a identificação da linha exata do código-fonte de uma falha. Checkmarx e Fortify fazem a varredura do código-fonte diretamente. O SAST de código-fonte da Checkmarx significa que nenhum build é necessário, permitindo varreduras mais rápidas em ciclos de desenvolvimento. A análise estática da Fortify também funciona no código-fonte, embora muitas vezes exija uma saída de build intermediária para certas análises (por exemplo, pode precisar de artefatos compilados ou bytecode para rastrear fluxos de dados de forma abrangente). Na prática, o processo de varredura da Fortify pode ser bastante complexo, enquanto a Checkmarx visa uma varredura de código mais direta.
Além do SAST, Veracode e Fortify fornecem Testes Dinâmicos de Segurança de Aplicações (DAST) para aplicações web em execução – Veracode Dynamic Analysis e Fortify WebInspect, respectivamente. A Checkmarx historicamente carecia de uma oferta DAST integrada, embora a nova plataforma Checkmarx One tenha introduzido algumas capacidades DAST (não tão testadas em campo quanto as outras). Para varredura de dependências open-source (SCA), todas as três agora têm soluções: Veracode Software Composition Analysis cobre bibliotecas de terceiros; Checkmarx tem CxSCA; Fortify integra SCA via uma parceria (Debricked no Fortify on Demand).
Lacunas de Cobertura: Uma área de divergência são os domínios de segurança mais recentes. Varredura de imagens de contêiner (verificando imagens Docker em busca de vulnerabilidades) e varredura IaC não são cobertos nativamente pela Veracode, e a Fortify não tem uma oferta proeminente nessa área. A Checkmarx, por outro lado, adicionou ambos – ela oferece varredura de segurança de Container e um scanner IaC (alimentado por sua ferramenta open-source KICS). Se você precisa escanear Kubernetes YAML, Terraform ou Dockerfiles em busca de configurações incorretas, a Checkmarx tem uma vantagem. Nenhuma das três possui varredura de Secrets integrada para coisas como chaves de API no código – você precisaria de outra ferramenta. Em resumo, Veracode = SAST + DAST + SCA, Checkmarx = SAST + SCA (+ IaC/Container), Fortify = SAST + DAST (+ SCA via addon). Cada uma cobre bem os fundamentos de AppSec, mas a cobertura mais moderna de "código para Cloud" é fragmentada.
Profundidade de Segurança: Todas as três possuem extensos conjuntos de regras de vulnerabilidade para linguagens comuns. Fortify, sendo uma pioneira, é frequentemente considerada como tendo uma das bases de conhecimento de vulnerabilidades mais extensas (pode sinalizar problemas obscuros e possui muitos verificadores). Veracode e Checkmarx também têm bibliotecas de vulnerabilidades abrangentes; a da Veracode inclui um foco em varredura orientada por políticas (você pode aplicar padrões e requisitos de conformidade facilmente), enquanto o motor da Checkmarx permite consultas personalizadas (você pode escrever regras personalizadas via CxQL para personalizar o que ele encontra). Resumindo: em termos de capacidade pura de encontrar vulnerabilidades, todas as três são ferramentas SAST renomadas – nenhuma o deixará completamente exposto a problemas do Top 10 OWASP, por exemplo. As diferenças são mais sobre a amplitude da cobertura (open source, runtime, etc.) e a usabilidade prática desses resultados (o que abordaremos a seguir).
Integração e Fluxo de Trabalho DevOps
Uma ferramenta de segurança é tão boa quanto seu encaixe no seu processo de desenvolvimento. A Checkmarx é geralmente vista como a mais amigável à integração para fluxos de trabalho de desenvolvimento. Ela oferece plugins para IDEs populares (Visual Studio, Eclipse, IntelliJ, VS Code, etc.), para que os desenvolvedores possam escanear código e obter resultados sem sair do editor. Ela também se integra com controle de versão (GitHub, GitLab, Bitbucket) e ferramentas de CI/CD como Jenkins, CircleCI, Azure DevOps – e assim por diante. Quer você execute on-prem ou use a Cloud da Checkmarx, ela pode se conectar ao seu pipeline para fazer um build falhar em bugs de alta gravidade ou criar tickets automaticamente. Esse foco em encontrar os desenvolvedores onde eles trabalham significa que a Checkmarx pode inserir verificações de segurança com menos atrito. Uma ressalva: alguns usuários notam diferenças entre as versões on-prem e SaaS – por exemplo, certos novos recursos ou UIs mais fluidas na Cloud – o que pode afetar a experiência de integração.
A Veracode, sendo uma plataforma SaaS, integra-se principalmente na etapa de CI/CD e via seu portal web. Você tipicamente faz upload do código (em forma compilada) através de um plugin ou script de pipeline para a plataforma da Veracode para varredura. Eles fornecem plugins Jenkins e APIs REST para automatizar isso. A Veracode também possui alguns plugins IDE (como uma extensão Visual Studio e um plugin IntelliJ) para desenvolvedores realizarem varreduras leves, mas estes não são tão aclamados quanto as integrações IDE da Checkmarx. Um sentimento comum é que a abordagem de integração da Veracode é mais centralizada: é ótima para aplicar varreduras no seu build principal, mas não tão interativa para desenvolvedores escrevendo código. Também é fortemente acoplada a certos ambientes – por exemplo, é conhecida por funcionar perfeitamente com pipelines GitHub se você usa GitHub, mas não suporta controle de versão on-prem porque a própria Veracode não implanta on-prem. Se você exige varredura no local, Veracode não é uma opção (sem implantação auto-hospedada). Essa natureza apenas Cloud simplifica a integração (nenhum servidor para manter), mas significa que seu código (em forma binária) deve ser enviado para os servidores da Veracode – um fator decisivo para alguns projetos sensíveis.
Fortify oferece pontos de integração semelhantes ao Checkmarx em teoria, mas tende a ser mais intensivo em mão de obra. Com o Fortify, muitas empresas configuram um servidor Fortify central (SSC – Software Security Center) e possivelmente distribuem scanners para as máquinas dos desenvolvedores. No passado, os desenvolvedores podiam executar varreduras Fortify via um cliente desktop ou plugin de CI e fazer upload dos resultados para o portal Fortify SSC. Existem plugins Jenkins, GitHub Actions e até plugins de IDE disponíveis (o Fortify tem plugins para Eclipse/VS, etc.), então ele pode integrar-se a CI/CD e IDEs de desenvolvedores. No entanto, a reputação do Fortify é que ele frequentemente exige mais etapas manuais ou experiência para ser configurado corretamente. Algumas equipes acabam com uma equipe de administração Fortify dedicada que lida com a execução de varreduras e o fornecimento de resultados aos desenvolvedores. Isso sugere que, embora a integração seja possível, o Fortify não parece tão contínuo em uma configuração DevOps de ritmo acelerado – é um pouco antiquado.
Em resumo, o Checkmarx se encaixa melhor em um fluxo de trabalho DevOps rápido com flexibilidade na integração e ferramentas voltadas para o desenvolvedor. O Veracode se integra bem no nível do pipeline, mas parece mais um passo separado governado pelas políticas da equipe de segurança (e é apenas na Cloud). O Fortify pode integrar, mas frequentemente precisa de esforço extra e não incentiva naturalmente o autoatendimento do desenvolvedor (muitas organizações o tratam como uma varredura controlada executada por engenheiros de segurança). Quanto mais sua equipe deseja segurança de autoatendimento incorporada ao desenvolvimento, mais você se inclina para o Checkmarx ou uma solução mais recente como o Aikido. Se sua prioridade é um ponto de verificação central e você não se importa com ciclos mais lentos, o Veracode ou o Fortify podem se encaixar, embora com algum atrito.
Precisão e Desempenho
Um dos maiores pontos fracos nos testes de segurança de aplicações são os falsos positivos – e aqui as ferramentas diferem nos seus históricos. Fortify tem sido frequentemente criticado pelas altas taxas de falsos positivos quando usado sem ajustes. Os utilizadores relatam «reclamações frequentes sobre falsos positivos do Fortify, em que um dia a verificação está limpa e no dia seguinte ele sinaliza novos problemas em código inalterado. Essa inconsistência e ruído podem frustrar os programadores. Fortify muita profundidade (tenta encontrar muitos tipos de problemas), mas isso pode significar mais triagem manual para separar os riscos reais do ruído. Ele também não filtra inerentemente vulnerabilidades conhecidas como seguras em bibliotecas de terceiros – Fortify não verifica automaticamente as bases de dados CVE para si sem um complemento, então pode ser que uma função insegura seja sinalizada, mas não seja informado que existe um patch conhecido, etc.
Checkmarx, por outro lado, é frequentemente elogiado por uma taxa de falsos positivos um pouco mais baixa (e é possível personalizar regras para ajustá-la). De acordo com as avaliações do G2, a taxa de falsos positivos Checkmarxé considerada melhor do que Fortify— um resumo observou que Checkmarx uma taxa mais baixa de falsos positivos, o que é muito importante para os programadores, enquanto a taxa de falsos positivos Fortify«não é tão favorável». Menos falsos alarmes significam que os programadores não começam a ignorar as descobertas de segurança. Dito isto, Checkmarx não Checkmarx imune a ruídos – alguns programadores sentiram que ele pode deixar passar certos problemas (falsos negativos) ou ainda relatar muitos problemas informativos como «vulnerabilidades». Ele atinge um equilíbrio razoável, mas requer algum ajuste e compreensão de seus resultados. A abordagem Checkmarxde analisar código não compilado significa que ela pode sinalizar algo como vulnerável que, na realidade, não é acessível na aplicação compilada (contexto que pode passar despercebido sem executar a aplicação). Por outro lado, a análise binária Veracodepode detectar problemas em dependências compiladas, mas também pode ter dificuldade em mapear as descobertas para as linhas de código exatas, fazendo com que os programadores tenham mais trabalho para descobrir a correção.
Veracode tem, em geral, uma reputação de precisão sólida após a realização da verificação inicial. Na verdade, eles realizam uma «verificação de base» inicial que pode levar dias, em parte para permitir que AppSec sua AppSec interna AppSec analise os resultados, caso tenha pago por esse serviço. A ideia é reduzir os falsos positivos envolvendo especialistas em segurança e fornecer uma linha de base limpa para o futuro. Isso é ótimo para a precisão — Veracode afirma que apresenta muito poucos falsos positivos nos seus resultados —, mas significa que a primeira verificação não é rápida. Alguns programadores ainda encontraram falsos positivos com Veracode nenhuma ferramenta é perfeita – por exemplo, programadores no HackerNews mencionam ter recebido alguns e-mails de falsos positivos inicialmente). Mas, em geral, a verificação Veracodeé madura e ajustada, especialmente para linguagens convencionais, resultando em boa precisão. Se uma organização não tem pessoal para triar manualmente as descobertas, a abordagem Veracodede menos descobertas, mas mais verificadas, pode ser atraente.
Em termos de desempenho (velocidade): Checkmarx, executado no código-fonte, geralmente consegue verificar mais rapidamente as alterações incrementais (e pode ser dimensionado adicionando mais máquinas/instâncias de verificação para verificações paralelas). As análises Veracodeenvolvem o upload de binários e, em seguida, a espera pelo processamento na nuvem – a espera pode ser uma desvantagem para equipas ágeis (algumas observaram «ciclos de feedback mais lentos» com Veracode). O desempenho Fortifydepende de como o implementa; pode ser bastante lento em bases de código muito grandes, a menos que ajuste a análise (Fortify opções para ajustar a profundidade da análise). Um utilizador do PeerSpot chegou a mencionar que a digitalização Fortify às vezes demora tanto ou é tão inconsistente que os resultados variam de um dia para o outro. Por outro lado, Fortify pode ser dimensionado com hardware suficiente e o seu mecanismo de digitalização é bastante poderoso – mas pode ser necessário dedicar servidores potentes para obter resultados oportunos em um grande monólito.
Em resumo, Veracode Checkmarx a produzir resultados mais precisos com ajustes moderados, enquanto Fortify detectar mais problemas em casos extremos, mas à custa de uma taxa mais alta de falsos positivos e tempos de verificação mais longos. Para um líder técnico, isso significa que Fortify exigir mais tempo da equipa para gerir os resultados, enquantoVeracode economizar tempo concentrando-se no que é importante (embora Veracode tempo após essa verificação inicial lenta). A precisão é vital — uma ferramenta que dá alarmes falsos com muita frequência será ignorada pelos programadores. É exatamente por isso que muitas equipas procuram alternativas que aproveitem técnicas modernas (como IA) para reduzir o ruído — que é a filosofia Aikido.
Cobertura e Escopo
Suporte a linguagens e estruturas: Veracode, Checkmarx e Fortify suporte a uma ampla variedade de linguagens de programação, abrangendo todas as mais comuns (Java, C#, JavaScript/TypeScript, Python, C/C++, Ruby, PHP etc.) e muitas outras menos comuns. Veracode suporte para mais de 30 linguagens, aproveitando a sua verificação binária para cobrir qualquer coisa que compile para um formato conhecido (incluindo ficheiros .APK do Android, assemblies .NET, etc.). Fortify suporta uma longa lista, incluindo linguagens mais antigas como COBOL e ASP clássico, devido à sua longa história empresarial. Checkmarx muitas linguagens modernas e acompanha as novas (por exemplo, adicionou suporte para linguagens como Go e Kotlin à medida que ganharam popularidade). Para a maioria das organizações, os três cobrirão as linguagens da sua pilha, a menos que tenha algo verdadeiramente esotérico.
Uma diferença pode ser a tecnologia legada e a mais recente: Fortify ter uma vantagem na tecnologia legada (porque as empresas que usavam Fortify verificar até mesmo coisas como código PL/SQL ou linguagens de mainframe com ele). Checkmarx Veracode bem as linguagens e estruturas mais recentes ( SCAVeracode, por exemplo, pode analisar dependências do Swift Package Manager, e Checkmarx lidar com estruturas JavaScript modernas, etc.). Se estiver a utilizar estruturas de nicho, convém verificar o conjunto de regras de cada ferramenta, mas, em geral, a amplitude da cobertura é comparável.
Tipos de vulnerabilidade: Todos os três cobrem as Top 10 OWASP categorias Top 10 OWASP CWE de forma abrangente. As categorias de vulnerabilidade Fortifysão extensas (e, por vezes, avassaladoras). Checkmarx Veracode abrangem uma ampla gama de tipos de bugs de segurança, desde injeção de SQL até configurações inseguras de cookies. Nenhuma dessas ferramentas se limita apenas a bugs de segurança — elas frequentemente sinalizam configurações inseguras no código (por exemplo, uso de algoritmos criptográficos fracos) e, às vezes, problemas de qualidade que podem levar a problemas de segurança. Fortify Veracode alguma sobreposição com a qualidade do código (Fortify verificadores para problemas de fiabilidade; Veracode algumas políticas de qualidade), mas o seu foco é a segurança. Checkmarx se mantém fiel às regras orientadas para a segurança (ao contrário de uma ferramenta puramente de qualidade como SonarQube, que encontra problemas no código).
Além do código: como mencionado, é na cobertura além do próprio código da aplicação que surgem as diferenças. Aqui está uma tabela comparativa rápida das áreas de cobertura:
Conformidade e relatórios: Uma parte do «âmbito» é se a ferramenta ajuda com estruturas de conformidade (PCI, OWASP, etc.). Veracode um forte suporte para relatórios de conformidade e gestão de políticas – pode definir políticas (por exemplo, «não são permitidas questões OWASP Top10 acima de gravidade média») e acompanhar a conformidade ao longo do tempo. Fortify oferece modelos de relatórios de conformidade e integra-se com sistemas GRC empresariais. Checkmarx também Checkmarx funcionalidades de conformidade, mas Veracode ter uma vantagem, dado o seu foco nas equipas de segurança (foi criada com a aplicação de políticas em mente). Se precisar de mostrar aos auditores que está a seguir um determinado padrão, qualquer uma das três pode ajudar, mas Veracode Fortify neste aspecto.
Escalabilidade do escopo: quando você tem centenas de aplicações, o modelo de nuvem Veracodelida com a escalabilidade por padrão (basta enfileirar mais varreduras na nuvem deles). Checkmarx exigirá que você dimensione os seus servidores de verificação ou use a oferta de nuvem deles para lidar com muitos projetos. Fortify pode ser dimensionado, mas geralmente precisa de infraestrutura e gerenciamento significativos para dezenas de aplicações (Fortify Demand pode descarregar isso para a nuvem deles se você usar o FoD). Portanto, se você tiver um portfólio de aplicações muito grande, considere como cada plataforma é dimensionada para cobrir todas elas. Veracode comprovado em grandes ambientes (mas você paga por cada verificação de aplicação), Fortify fazer isso, mas pode se tornar um grande projeto interno, Checkmarx bem, mas você deve arquitetá-lo corretamente ou optar pelo SaaS deles.
Experiência do Desenvolvedor
No que diz respeito ao uso diário por desenvolvedores, todas as três ferramentas apresentam vulnerabilidades através de painéis e integrações IDE, mas a usabilidade e o fator de frustração diferem. Checkmarx posiciona-se como a mais centrada no programador. A sua interface de utilizador é relativamente limpa e permite aos programadores filtrar e classificar problemas com facilidade. Os programadores podem obter resultados nas ferramentas que utilizam (IDE, SCM, CI), o que reduz a mudança de contexto. Checkmarx oferece o Codebashing, um módulo de formação integrado, para ajudar os programadores a aprender sobre os erros de segurança específicos que cometeram – um toque agradável para transformar as descobertas emmomentos de aprendizagem. A curva de aprendizagem para Checkmarx básica Checkmarx não é íngreme; executa-se uma verificação e obtém-se uma lista de problemas com trechos de código e orientações de correção. O uso avançado (como escrever consultas personalizadas) é mais complexo, mas não obrigatório para a maioria. Uma reclamação foi que Checkmarx no local parecia desatualizada (um utilizador brincou que era«diretamente de 1997»em termos de aparência). A sua interface de nuvem mais recente é mais moderna. No geral, os programadores geralmente consideram Checkmarx utilizável, embora possam reclamar sobre falsos positivos ou o tempo para gerir os resultados em projetos maiores.
Veracodeé um pouco mais mista. A plataforma tem como tradição servir equipas de segurança, por isso o seu portal web é rico em dados, relatórios de políticas e configurações administrativas – o que pode sobrecarregar um programador que apenas deseja corrigir o seu bug. Veracode a sua experiência de desenvolvimento ao fornecer um plugin de verificação IDE e integrações de pipeline, mas alguns programadores consideram o processo menos interativo. Muitas vezes, é necessário iniciar sessão no Veracode para ver informações detalhadas sobre as falhas, e os resultados nem sempre apontam diretamente para uma linha do código-fonte (especialmente se o problema estiver numa biblioteca compilada). Além disso, como Veracode exigir o upload da compilação completa, um programador que esteja à espera para ver se o seu commit recente introduziu novas falhas pode ter de aguardar por um espaço de verificação e processamento. Este atraso pode reduzir a rapidez que os programadores esperam hoje em dia (gostamos de linting instantâneo e feedback rápido). A interface do utilizador Veracodeé profissional, mas pode parecer um pouco complicada para triar muitas questões — por exemplo, alguns utilizadores desejam mais personalização nos relatórios e filtragem mais fácil (Veracode esses recursos, mas não são tão intuitivos). No lado positivo, Veracode orientação para correção e até serviços de consultoria; um programador pode obter ajuda de Veracode (se pagar) para entender uma descoberta. Portanto, a experiência para um programador novo em segurança pode realmente ser útil nesse sentido. Só não espere que os programadores amem a ferramenta — ela é vista como necessária, mas não agradável para os programadores, para sermos honestos.
Fortify é frequentemente visto como o mais complicado para os programadores. Historicamente, as empresas executavam Fortify e, em seguida, exportavam um PDF ou enviam um ficheiro Fortify (Fortify Results) aos programadores – o que não é exatamente amigável para os programadores. Fortify um portal web central (SSC) onde os programadores podem registar problemas como corrigidos ou marcar falsos positivos, mas a interface do utilizador e o fluxo de trabalho são frequentemente descritos como desatualizados ou pouco intuitivos em comparação com as ferramentas modernas. Como um engenheiro de segurança educadamente colocou, a interface Fortifypermite que você faça o que precisa, mas não ganha nenhum prémio de experiência do utilizador. Os programadores que usam Fortify estar a usar o Fortify Wizard ou um plugin IDE para verificar o código; essas ferramentas funcionam, mas podem tornar o IDE mais lento e não são tão elegantes quanto as ofertas mais recentes. Além disso, Fortify a apresentar um grande volume de resultados se não configurar filtros, o que pode sobrecarregar os programadores («Por onde começo?»). A curva de aprendizagem é íngreme — os programadores podem precisar de formação para usar eficazmente o Workbench Fortifypara triar os resultados. Por outro lado, os resultados Fortifysão detalhados e, para aqueles que investem tempo nele, tornam-se gerenciáveis. Mas esperar que os programadores adotem Fortify com entusiasmo e Fortify resistência é uma ilusão — muitos programadores o veem como uma tarefa obrigatória imposta pela segurança. Em parte, é por isso que algumas empresas agora complementam ou substituem Fortify ferramentas mais amigáveis para os programadores.
Falsos positivos e moral dos desenvolvedores: Temos que mencionar novamente – nada prejudica mais a experiência dos desenvolvedores do que falsos positivos e ruído. Se Checkmarx Fortify os desenvolvedores com centenas de "possíveis problemas", dos quais apenas alguns são realmente importantes, os desenvolvedores perderão a confiança e começarão a ignorar a ferramenta. Checkmarx isso e promoveu recursos para reduzir o ruído. A resposta Fortifygeralmente é usar suas ferramentas de auditoria para suprimir manualmente os falsos alertas conhecidos (novamente, trabalho extra). A estratégia Veracodeé reduzir o ruído antecipadamente e permitir a marcação de mitigações, o que pelo menos demonstra compreensão das dificuldades dos desenvolvedores.
Adequação ao fluxo de trabalho de desenvolvimento: outro fator é se os desenvolvedores podem incorporar facilmente correções e realizar novos testes. Com Checkmarx, um desenvolvedor pode corrigir o código, executar uma verificação local e verificar se o problema foi resolvido. Com Veracode, o fluxo típico pode ser: confirmar o código, executar a CI, fazer o upload para Veracode, aguardar e, em seguida, verificar — um pouco mais lento. Com Fortify, talvez o desenvolvedor execute uma Fortify local Fortify , o que pode demorar um pouco, ou aguarde a próxima verificação agendada pela equipa de segurança — o que não é ideal. Portanto, para capacitar os desenvolvedores a realizarem correções de segurança, Checkmarx ou uma ferramenta como Aikido) oferece um controle mais direto.
Em resumo, da perspetiva de um programador: Checkmarx a menos odiada – ela tenta integrar-se no mundo deles e reduzir os pontos fracos. Veracode é respeitado, mas um pouco distante – os programadores sentem-no como um obstáculo externo que têm de ultrapassar, e não como um amigo útil no IDE. Fortify é poderoso, mas pesado – muitas vezes parece que se está a usar uma ferramenta empresarial antiga, e muitos programadores preferem esperar por um resumo da equipa de segurança em vez de Fortify envolverem ativamente com Fortify . Se quiser que os programadores adiram à AppSec, é fundamental minimizar o atrito e o ruído. É por isso que muitos estão à procura de soluções mais recentes (como Aikido) que priorizam a experiência do programador tanto quanto a cobertura de segurança.
Preços e Manutenção
Todas as três plataformas são produtos comerciais com preços empresariais, e nenhuma delas pode ser considerada barata. Na verdade, o custo é uma reclamação comum em todos os casos:
- Veracode geralmente cobra com base no número de aplicações, linhas de código e frequência de verificação (com complementos para recursos adicionais). As avaliações frequentemente mencionam Veracode «um produto muito caro». As empresas menores raramente podem pagar por ele. Ele é voltado para empresas de médio a grande porte com orçamento para segurança. Não há nível gratuito; você paga pela qualidade e amplitude. A vantagem é que você não precisa manter a infraestrutura — o modelo SaaS significa que o custo inclui o gerenciamento dos servidores e atualizações. Mas se você tiver centenas de aplicações ou milhões de linhas de código, a conta pode subir rapidamente (valores de seis dígitos não são incomuns para licenças empresariais). O preço Veracodeé premium – uma revisão por pares afirmou categoricamente que é «caro demais» para o que oferece, embora reconheça que a qualidade é alta. Além disso, alguns recursos, como eLearning ou testes de penetração manuais, são extras.
- Checkmarx também não é barato. Normalmente, a licença é concedida por utilizador ou por módulo de base de código. Um relatório indicou que, para cerca de 250 programadores, o custo era de cerca de US$ 500 mil, o que dá uma ideia aproximada de como podem ser os negócios empresariais. Checkmarx vários módulos (SAST, SCA, etc.) que podem ser licenciados separadamente ou em pacote. Se optar pela versão local, lembre-se de que precisará de alocar servidores (o que é um custo indireto, embora não seja muito elevado neste contexto). A oferta SaaS transforma isso numa taxa de subscrição. Checkmarx também Checkmarx tem realmente uma edição «comunitária» (exceto algumas ferramentas gratuitas, como um KICS de código aberto limitado para varredura IaC). Portanto, em termos de orçamento, considere que está no mesmo nível da Veracode. Alguns dizem que o investimento se justifica pela cobertura de segurança, mas pode ser difícil de aceitar para organizações menores.
- Fortify Os preços podem variar porque muitas vezes é vendido como parte de contratos maiores (especialmente na época da HP/Micro Focus). Tradicionalmente, Fortify era licenciado por número de linhas de código, por verificação ou por posto de trabalho – e era caro. Fortify Demand (o SaaS) pode ser uma assinatura por aplicação ou por pacote empresarial. Não há preços públicos, mas é um software empresarial – espere preços empresariais. Fortify tem custos ocultos em termos de manutenção: se for auto-hospedado, você precisa de pessoas para gerenciar atualizações, ajustar regras, manter os servidores, etc. Muitas organizações têm literalmente um Fortify dedicado ou contratam consultores para a implementação. Isso aumenta o custo total de propriedade. O lado positivo é que a licença local Fortify, uma vez comprada, pode fazer varreduras ilimitadas sem custo adicional, e você não está a enviar código para terceiros (importante para alguns). Mas se você não renovar continuamente o suporte, a ferramenta pode ficar rapidamente desatualizada à medida que novas vulnerabilidades e linguagens surgem.
Os custos de suporte são outra consideração: os três fornecedores oferecem serviços de suporte e consultoria. O suporte Veracode Checkmarx Veracode pode ter um custo adicional. O suporte padrão Fortifynormalmente está incluído na renovação da licença, mas poderá ter um custo adicional para itens como formação.
Os preçosAikido são mais simples e previsíveis. Embora não divulguemos valores exatos aqui, Aikido de seu modelo de preços fixos e transparentes, que costuma ser significativamente mais acessível em escala do que as ferramentas tradicionais. Não há taxas adicionais surpresa para cada recurso extra — você obtém a plataforma completa sem pagar a mais por nada. Para um líder técnico, isso significa um orçamento mais fácil e a possibilidade de cobrir toda a sua equipa de desenvolvimento e base de código sem gastar muito. Em comparação com Veracode Checkmarx «têm um preço premium» para funcionalidades empresariais, Aikido oferece muito mais valor pelo dinheiro. Foi concebida para ser uma plataforma única que pode substituir várias ferramentas (SAST, SCA, DAST, etc.), pelo que as empresas também poupam com a consolidação.
Em resumo, esteja preparado: Veracode, Checkmarx e Fortify exigem um orçamento considerável (e seus custos geralmente aumentam com o tamanho da sua organização). Se você tem uma equipe menor, eles podem estar fora do seu alcance ou ser um exagero. Se você faz parte de uma organização maior, considere não apenas o licenciamento, mas também a mão de obra para gerenciar a solução que escolher. E lembre-se, uma ferramenta que economiza tempo do desenvolvedor ou previne uma violação pode se pagar – mas apenas se for usada de forma eficaz. É por isso que muitos estão buscando a nova geração, como o Aikido, que promete um custo total de propriedade mais baixo ao reduzir a proliferação de ferramentas e o trabalho administrativo, além de ser mais acessível inicialmente.
Prós e Contras de Veracode, Checkmarx e Fortify
Veracode – Prós:
- Conjunto AST abrangente: Oferece análise estática, dinâmica e de composição em uma única plataforma para uma ampla cobertura de vulnerabilidades.
- Governança de segurança robusta: Excelente para aplicação de políticas, rastreamento de conformidade e relatórios de nível executivo (PCI, OWASP, etc.) integrados.
- Conveniência da Cloud: A entrega SaaS significa nenhuma infraestrutura para gerenciar; escala facilmente para muitos aplicativos e inclui opções de suporte especializado para remediação.
- Varredura de binários detecta mais: A análise de código compilado pode encontrar problemas em componentes integrados e garantir que bibliotecas de terceiros sejam varridas como parte de toda a aplicação.
Veracode – Contras:
- Sem opção on-premise: Exige o upload de binários de código para a Cloud; não é viável para bases de código altamente sensíveis que devem permanecer on-premise.
- Tempo de resposta da varredura lento: As varreduras iniciais podem ser lentas (a revisão da linha de base pode levar dias) e mesmo varreduras subsequentes adicionam latência ao pipeline, atrasando o feedback para os desenvolvedores.
- Integração limitada para desenvolvedores: Foca mais na varredura centralizada do que no feedback dentro da IDE – os desenvolvedores frequentemente precisam usar o portal, e a experiência é voltada para equipes de segurança em vez do fluxo de trabalho de desenvolvimento.
- Alto custo para empresas: O preço está no lado premium (“muito caro” por vários relatos) e pode ser difícil de justificar para equipes menores.

Checkmarx – Prós:
- Análise estática amigável para desenvolvedores: Varre o código-fonte sem a necessidade de build, proporcionando feedback mais rápido e integração mais fácil em CI/CD e IDEs.
- Implantação flexível: Disponível tanto on-premise quanto SaaS – adequado para pipelines na Cloud ou ambientes auto-hospedados, conforme necessário.
- Ampla cobertura de linguagens e segurança: Suporta muitas linguagens e cobre SAST e SCA, além de extras como IaC e varredura de segurança de contêineres para um AppSec mais holístico.
- Customizável e extensível: Permite regras de consulta personalizadas e possui recursos como treinamento Codebashing; pode ser adaptado aos requisitos de segurança específicos de uma organização.
Checkmarx – Contras:
- Falsos positivos ainda ocorrem: Embora geralmente melhor que alguns concorrentes, pode relatar problemas que não são verdadeiros, exigindo ajuste manual e tempo do desenvolvedor para filtrar o ruído.
- UX on-premise está desatualizada: A interface e o fluxo de trabalho mais antigos podem parecer desajeitados (um usuário comparou-o a software dos anos 90); alguns recursos avançados são apenas na Cloud, criando inconsistência.
- Sem DAST completo ou proteção em tempo de execução: Principalmente uma ferramenta de análise estática – falta um componente de teste dinâmico maduro e coisas como varredura de segredos, portanto, não cobre riscos de aplicativos em tempo real sem ferramentas adicionais.
- Caro para grandes equipes: Recursos empresariais vêm com um preço premium (por exemplo, na faixa de ~$500k para algumas centenas de desenvolvedores), e executá-lo on-premise incorre em custos de manutenção para servidores e atualizações.

Fortify – Prós:
- Varredura profunda e completa: Motor SAST muito abrangente com um dos mais amplos conjuntos de regras de vulnerabilidade; capaz de encontrar problemas de segurança obscuros graças a anos de aprimoramento.
- Recursos de nível empresarial: Relatórios robustos, modelos de conformidade e integração com fluxos de trabalho empresariais (ALM, rastreadores de bugs) para apoiar os processos de grandes organizações.
- Testes dinâmicos incluídos: Oferece uma solução DAST completa (WebInspect) e pode ser uma solução completa para testes de aplicativos estáticos e dinâmicos. Fortify tem sido líder no Gartner MQ por mais de 11 anos, indicando um nível de confiança em suas capacidades gerais (se não em sua agilidade).
- Implantação flexível: Pode ser executado completamente on-premises para controle total dos dados, ou usado como Fortify on Demand SaaS. Isso permite atender a requisitos rigorosos de privacidade de dados, mantendo a varredura interna, se necessário.
Fortify – Contras:
- Alto ruído de falsos positivos: Conhecido por relatar muitos problemas potenciais – requer uma triagem significativa. Os usuários frequentemente reclamam de varreduras que identificam achados sem alteração de código. Isso pode sobrecarregar os desenvolvedores com não-problemas.
- Curva de aprendizado íngreme e esforço de uso: Configuração e uso complexos – frequentemente exige administradores ou consultores especializados. A interface do usuário e as ferramentas parecem desajeitadas, o que pode prejudicar a adoção pelos desenvolvedores e retardar o processo.
- Manutenção intensiva: O Fortify auto-hospedado exige manutenção (servidores, bancos de dados, atualizações). Muitas organizações precisam de uma equipe dedicada para gerenciar o Fortify, aumentando o custo e a complexidade. A ferramenta em si pode ser intensiva em recursos e mais lenta em grandes bases de código se não for otimizada.
- Integração limitada com fluxos de trabalho de desenvolvimento modernos: Embora existam integrações, o Fortify não se encaixa tão suavemente nas práticas ágeis de DevOps. Os desenvolvedores podem tratá-lo como um portão periódico em vez de um assistente contínuo, levando a que a segurança seja isolada em vez de incorporada.
Aikido Security: A Melhor Alternativa
Aikido Security é a solução moderna que une tudo sem a bagagem. É uma plataforma tudo-em-um cobrindo SAST, DAST, SCA, IaC, Container, Secrets, segurança na nuvem – o que você precisar – em um só lugar. Ao contrário das ferramentas legadas, o Aikido é construído pensando no desenvolvedor: ele se integra perfeitamente às suas IDEs, repositórios e pipelines de CI/CD, fornecendo feedback instantâneo com ruído mínimo. A plataforma usa automação inteligente (até mesmo IA) para redução de falsos positivos e Auto-triage de achados, para que sua equipe se concentre apenas em problemas reaist. Com sugestões de AI Autofix, o Aikido pode até ajudar a gerar correções para vulnerabilidades, acelerando a remediação.
Chega de fazer malabarismos com várias ferramentas ou se afogar em alertas – a abordagem unificada do Aikido significa que uma única ferramenta oferece visibilidade total em código e Cloud, com contexto para priorizar o que mais importa. É entregue como um SaaS amigável para desenvolvedores com preços simples e previsíveis (sem adicionais surpresa), tornando-o significativamente mais acessível em escala do que Veracode, Checkmarx ou Fortify. Em resumo, o Aikido oferece menos falsos positivos, varreduras mais rápidas e uma experiência de desenvolvedor muito melhor do que a velha guarda. É a alternativa direta e amada pelos desenvolvedores para equipes que desejam segurança de ponta sem as dores de cabeça usuais.
Na batalha de Veracode vs Checkmarx vs Fortify, o vencedor, na verdade, não é nenhum deles – é o novo concorrente que combina seus pontos fortes e corrige suas fraquezas. Esse é o Aikido: uma ferramenta que finalmente torna a segurança sem atrito para desenvolvedores e líderes de segurança, para que você possa entregar código seguro e avançar rapidamente.
Inicie um teste gratuito ou solicite uma demonstração para explorar a solução completa.



