Se você é responsável pelo AppSec ou CloudSec da sua organização, você provavelmente avaliou Snyk e Wiz, ou pelo menos debateu qual deles sua equipe realmente precisa. Ambas as plataformas são amplamente adotadas e frequentemente consideradas quando as organizações buscam fortalecer sua postura de segurança.
Embora sejam frequentemente mencionados nas mesmas conversas, escolher entre eles nem sempre é fácil. As equipes de segurança de hoje são esperadas para proteger tanto aplicações quanto ambientes Cloud, tudo isso enquanto apoiam fluxos de trabalho de desenvolvimento ágeis.
De acordo com o relatório Estado da IA em Segurança e Desenvolvimento de 2026 da Aikido Security, 93% das equipes têm dificuldade em integrar a segurança de aplicações com a segurança na Cloud, muitas vezes resultando em ferramentas fragmentadas e pontos cegos de segurança.
Neste artigo, compararemos Snyk e Wiz lado a lado, destacaremos onde eles se sobrepõem e ajudaremos você a entender qual ferramenta se alinha melhor com seus objetivos de segurança e desenvolvimento.
TL;DR
A Aikido Security combina os pontos fortes essenciais que as organizações buscam em ferramentas como Snyk e Wiz, sem a complexidade de usar ambos. Ela reúne a cobertura de código, dependências e Containers do Snyk com a visibilidade Cloud e insights de risco do Wiz, ao mesmo tempo em que aborda pontos cegos, proliferação de ferramentas e alertas ruidosos.
O resultado? Onboarding acelerado, melhor gerenciamento de riscos e visibilidade mais ampla.
Para startups e empresas, os pilotos da Aikido Security se destacam consistentemente graças à sua cobertura de ponta a ponta, priorização de riscos impulsionada por IA e sua capacidade de substituir múltiplas ferramentas dentro de um fluxo de trabalho único, centrado em segurança e amigável ao desenvolvedor.
Comparativo Rápido de Recursos: Snyk vs Wiz vs Aikido Security
O que é Wiz?
Wiz é uma plataforma de segurança cloud-native conhecida por seu foco em infraestrutura Cloud. Ela escaneia ambientes Cloud (AWS, Azure, GCP) em busca de configurações incorretas, vulnerabilidades e Secrets em workloads e serviços. E utiliza seu "Security Graph" proprietário para conectar riscos da camada de aplicação no código ao seu impacto potencial no runtime e na infraestrutura Cloud.
Prós:
- Wiz oferece ampla visibilidade na infraestrutura Cloud
- Ele se conecta via APIs Cloud.
- Ele prioriza riscos pela explorabilidade
- Construído para ambientes complexos e suporta todos os principais provedores Cloud.
Contras:
- É focado principalmente no ambiente corporativo
- Carece de capacidades DAST nativas
- É projetado para equipes de segurança.
- Integração limitada com fluxos de trabalho de desenvolvimento (IDEs, verificações de PR).
- Curva de aprendizado acentuada
- Usuários relataram sua interface de usuário (UI) e de consulta como não intuitiva ou complexa.
- Alto volume de alertas
- Pode exigir ferramentas complementares para cobertura total de AppSec.
- Usuários relataram problemas na integração com sistemas híbridos/legados
O que é Snyk?
Snyk é uma plataforma de segurança de aplicações. Inicialmente, ganhou destaque ao escanear dependências de código aberto em busca de vulnerabilidades conhecidas (SCA), e, posteriormente, expandiu-se para escanear código proprietário (SAST), Containers e templates IaC. Ele se integra diretamente em ambientes de desenvolvimento (IDEs) e plataformas CI/CD (GitHub, GitLab) para que os desenvolvedores recebam feedback de segurança precocemente, shifting security left.
Prós:
- Snyk se integra a IDEs, repositórios Git e pipelines de CI/CD.
- Possui um robusto banco de dados de vulnerabilidades.
- Oferece remediação acionável (sugestões de correção, pull requests).
- Monitora e alerta as equipes sobre novas vulnerabilidades.
Contras:
- Curva de aprendizado acentuada para novos usuários.
- Os tempos de varredura podem ser lentos em grandes repositórios.
- Falsos positivos.
- Os módulos do Snyk não são totalmente unificados, e atingir cobertura total requer add-ons empresariais.
- É conhecido por sobrecarregar os desenvolvedores com alertas de baixa prioridade.
- As sugestões de correção podem parecer genéricas e não totalmente adaptadas ao código.
- Pode ter dificuldade com bases de código proprietárias ou altamente especializadas.
- Sua análise estática tem um limite de tamanho de arquivo de 1 MB.
- O preço pode ser caro.
Comparação Recurso por Recurso
Capacidades de Varredura de Segurança
Snyk: Snyk cobre uma ampla gama de tipos de AppSec: SAST (análise estática de código para vulnerabilidades no código-fonte), SCA (análise de dependências de código aberto), varredura de imagens de contêiner e verificações de IaC. Essa ampla cobertura significa que o Snyk pode encontrar padrões de codificação inseguros em aplicações, bibliotecas npm vulneráveis ou scripts Terraform mal configurados, tudo em uma única plataforma.
Wiz: Wiz, por outro lado, especializa-se em varredura de Cloud e infraestrutura. Ele usa sua plataforma integrada de Cloud Security Posture Management (CSPM) para identificar configurações incorretas e configurações de risco em serviços de Cloud e cargas de trabalho. Recentemente, adicionou varredura de código-fonte (SAST) via Wiz Code, mas não possui um motor DAST nativo.
Em resumo, Snyk é mais forte na varredura em nível de código, enquanto Wiz cobre o ângulo de Cloud e infraestrutura mais profundamente.
Integração e Fluxo de Trabalho DevOps
Para que uma ferramenta de segurança tenha sucesso, ela deve se integrar perfeitamente ao fluxo de trabalho da sua equipe.
Snyk: Snyk integra-se perfeitamente com ferramentas de desenvolvedor, desde plugins de IDE até verificações de pull request do GitHub/GitLab e hooks de pipeline de CI. Desenvolvedores recebem alertas em tempo real enquanto codificam, bem como correções com um clique. Essa abordagem centrada no desenvolvedor significa que o Snyk pode ser adotado por equipes de engenharia com atrito mínimo.
Wiz: Wiz, por outro lado, é voltado para engenheiros de Cloud e segurança. Ele se conecta às suas contas Cloud (usando funções somente leitura ou APIs) e monitora continuamente os recursos. Possui integrações limitadas para desenvolvedores e exige que os desenvolvedores façam login no console do Wiz para investigar problemas.
Em resumo, Snyk se encaixa naturalmente em pipelines DevOps, enquanto Wiz é mais adequado para fluxos de trabalho SecOps.
Precisão e Falsos Positivos
Uma das principais reclamações sobre scanners de segurança é o ruído, seja de falsos positivos ou de altos volumes de alertas.
Snyk: Snyk, com sua abordagem voltada para o desenvolvedor, investiu na redução de ruído (usando sua DeepCode AI) para melhorar a análise estática. No entanto, usuários ainda relatam que o Snyk tende a sobrecarregar as equipes com descobertas de baixa prioridade ou falsos positivos, especialmente com certas linguagens. Ajustes são frequentemente necessários para filtrar o “ruído”.
Wiz: Ao focar no contexto Cloud, Wiz prioriza as descobertas com base no risco real. Ele correlaciona vulnerabilidades com o recurso afetado para determinar se ele está realmente exposto ou é crítico. Dito isso, as novas capacidades de varredura de código do Wiz não foram exaustivamente testadas quanto ao ruído, e a importação de resultados de ferramentas SAST externas poderia introduzir alguma duplicação ou falsos positivos se não for bem gerenciada.
Em geral, Wiz gera menos falsos positivos em problemas de configuração de Cloud, enquanto Snyk sinaliza mais problemas potenciais no código. Ambas as ferramentas, no entanto, ainda exigem ajustes...
Cobertura e Escopo
Snyk: Snyk suporta uma ampla gama de linguagens de programação e frameworks (para SAST e SCA), incluindo Java, JavaScript/Node.js, Python, .NET, Ruby, Go e muito mais. Também suporta registros de Container e formatos IaC (como Terraform, CloudFormation e manifestos Kubernetes). No entanto, não cobre ambientes Cloud em tempo real ou redes.
Wiz: Wiz oferece ampla cobertura de infraestrutura Cloud: pode escanear máquinas virtuais, clusters Kubernetes, funções serverless, bancos de dados e muito mais em AWS, Azure e GCP. As novas capacidades de varredura de repositórios do Wiz estendem seu alcance para código e IaC em controle de versão, mas para análise dinâmica de código (DAST) precisa ser integrado com ferramentas de terceiros.
Se sua stack é fortemente centrada em Cloud (microsserviços, implantações multi-cloud), Wiz garante que você tenha visibilidade nessa camada. Por outro lado, se você precisa verificar exaustivamente código e dependências pré-implantação, Snyk tem a vantagem nesse aspecto. Vale ressaltar que nenhuma das ferramentas oferece cobertura de ponta a ponta. Com muitas organizações acabando por usar plataformas como Aikido Security que oferecem cobertura de ponta a ponta, desde o código-fonte até as configurações de Cloud.
Experiência do Desenvolvedor
Snyk: Snyk foi desenvolvido pensando nos desenvolvedores . Sua Interface de Usuário (UI) e integrações apresentam os resultados de forma amigável para o desenvolvedor, por exemplo, mostrando a linha exata de código ou dependência que introduziu uma vulnerabilidade, com orientações claras para corrigi-la. Ele também pode abrir pull requests (PRs) de correção automática. No entanto, usuários relataram que a plataforma é desajeitada, com múltiplos módulos (Snyk Code, Snyk Open Source) tendo recursos sobrepostos, e algumas funcionalidades disponíveis apenas em planos de nível superior.
Wiz: A plataforma do Wiz é voltada para equipes de segurança, oferecendo um dashboard unificado de segurança na Cloud com visualização baseada em grafos de ativos e problemas. Para desenvolvedores que desejam corrigir bugs em códigos, o console do Wiz pode parecer opressor ou não diretamente relevante, com alguns usuários descrevendo a interface do Wiz como confusa e não intuitiva.
Em geral, os desenvolvedores consideram o Snyk mais acessível e fácil de navegar, enquanto o Wiz é tipicamente operado por equipes de SecOps ou Cloud que então comunicam suas descobertas diretamente aos desenvolvedores.
Preços e Manutenção
Snyk: Snyk é uma oferta SaaS com um modelo de precificação por desenvolvedor. Possui uma camada gratuita para projetos open-source, mas à medida que você escala, provavelmente precisará de planos pagos que podem aumentar significativamente à medida que mais módulos são adicionados. Para muitos recursos avançados (relatórios avançados, varredura on-premise, funções personalizadas), o Snyk exige planos de nível superior.
Do ponto de vista de manutenção, sua arquitetura baseada em Cloud significa que sua configuração é simples e não requer manutenção de infraestrutura.
Wiz: Wiz, em contraste, visa empresas e geralmente é precificado com base no tamanho do seu ambiente de Cloud (por exemplo, número de ativos de Cloud ou cargas de trabalho). Não há camada gratuita; você passa pelas vendas para uma cotação personalizada. Wiz é entregue como um SaaS, com sensores opcionais para implantação on-premise, então sua manutenção operacional é leve, mas mais tempo será investido na integração de contas de Cloud e no ajuste de políticas.
No geral, o Snyk pode parecer mais barato inicialmente, mas pode rapidamente se tornar caro ao escalar, enquanto o Wiz é um investimento pesado desde o início.
Aikido oferece um modelo de precificação mais simples e transparente – fixo e previsível – e é significativamente mais acessível em escala do que Snyk ou Wiz.
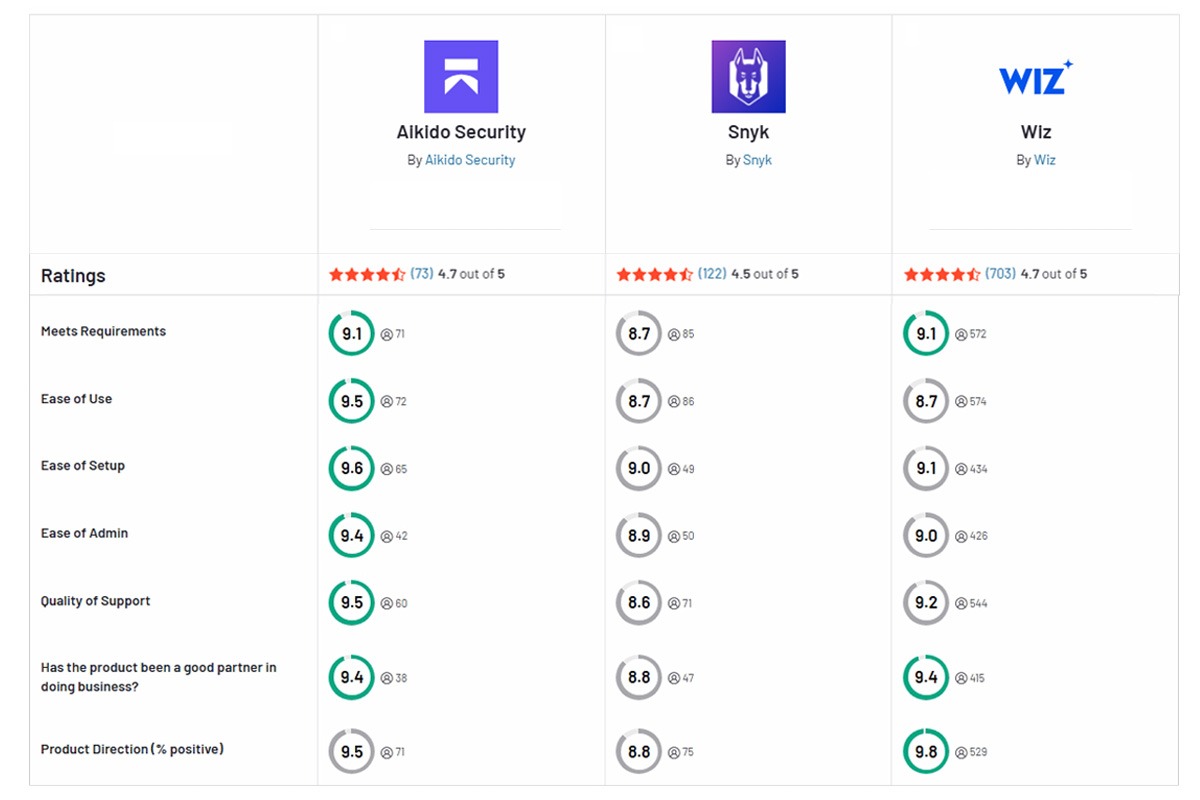
Para ajudar você a comparar os recursos de ambas as ferramentas, a tabela abaixo os resume para você.
Aikido Security: A Melhor Alternativa
Aikido Security é uma plataforma de segurança impulsionada por IA, construída para equipes que desejam forte segurança de aplicação e segurança na nuvem sem sacrificar a experiência do desenvolvedor. Ela vai além da varredura do Snyk em código, dependências, Containers e IaC e a combina com o contexto de Cloud e a visibilidade de riscos do Wiz, tudo dentro de um único workflow.
Seu motor de IA correlaciona descobertas entre as camadas de aplicação e Cloud e realiza Reachability analysis para identificar vulnerabilidades que são verdadeiramente exploráveis, reduzindo ruído e tempo gasto na triagem de alertas. A Aikido Security também oferece recursos de remediação automatizada, como pull requests de correção automatizada e correções com um clique para vulnerabilidades identificadas.
As equipes podem começar com qualquer módulo, SAST, SCA, varredura IaC, DAST, segurança em tempo de execução, varredura de contêineres, detecção de segredos ou qualidade de código, e habilitar módulos adicionais à medida que crescem.
Com precificação fixa e uma camada gratuita para sempre, o Aikido Security oferece AppSec e Segurança na Cloud de ponta a ponta sem a complexidade ou o custo de operar Snyk e Wiz.
Quer melhorar a segurança da sua aplicação e na nuvem? Comece seu teste gratuito ou agende uma demonstração com o Aikido Security hoje.
FAQ
Como Snyk e Wiz se integram com pipelines de CI/CD populares?
O Snyk se integra diretamente com plataformas como GitHub Actions, GitLab CI, Jenkins e Bitbucket, permitindo varreduras automatizadas de código, dependências e contêineres durante builds e pull requests. Enquanto o Wiz se conecta a pipelines de CI/CD através de APIs e conectores de nuvem, com foco na segurança de cargas de trabalho na nuvem.
Como plataformas de segurança na nuvem como Snyk e Wiz protegem as organizações?
O Snyk ajuda a proteger aplicações varrendo código, dependências de código aberto, contêineres e configurações IaC em busca de vulnerabilidades. O Wiz, por outro lado, protege cargas de trabalho na nuvem e ambientes de tempo de execução detectando configurações incorretas, permissões arriscadas e lacunas de conformidade. Plataformas como o Aikido Security combinam essas capacidades, fornecendo cobertura de segurança de ponta a ponta em código, dependências, contêineres e infraestrutura de nuvem.
Como Snyk se compara a Wiz em termos de detecção de vulnerabilidades?
O Snyk é forte na detecção de vulnerabilidades em código, bibliotecas de código aberto e imagens de contêineres. Enquanto o Wiz se especializa na identificação de configurações incorretas na nuvem, riscos de tempo de execução e problemas de CSPM. Ferramentas como o Aikido Security correlacionam vulnerabilidades em múltiplas camadas, reduzindo o ruído e fornecendo aos desenvolvedores orientação acionável.
Como Snyk e Wiz lidam com a segurança de contêineres de forma diferente?
O Snyk varre imagens de contêineres antes da implantação para detectar pacotes inseguros ou configurações incorretas. O Wiz foca no monitoramento em tempo de execução de contêineres e cargas de trabalho na nuvem para identificar riscos em produção. Plataformas como o Aikido Security combinam ambas as abordagens, ligando a varredura de contêineres ao contexto de código e IaC para proteger tanto os ambientes de desenvolvimento quanto os de tempo de execução.
Por que escolher a ferramenta certa de segurança na nuvem é importante para as empresas?
Selecionar a ferramenta de segurança na nuvem correta garante que todas as partes do seu ambiente, código, dependências, Containers e infraestrutura Cloud, estejam devidamente protegidas sem desacelerar o desenvolvimento. A ferramenta errada pode deixar pontos cegos, gerar muitos alertas falsos ou complicar os fluxos de trabalho. Plataformas como a Aikido Security oferecem uma solução amigável para desenvolvedores que equilibra cobertura, precisão e orientação acionável.
Você também pode gostar:
- 5 Alternativas ao Snyk e Por Que São Melhores
- Melhores Alternativas ao SonarQube em 2026
- Comparativo Snyk vs Trivy em 2026
- As 10 Principais ferramentas SAST com IA em 2026
- Os 13 Melhores Scanners de Vulnerabilidades de Código em 2026
- Comparação Snyk vs SonarQube em 2026
- Principais Scanners de Infrastructure as Code (IaC)



